With the majority of data breaches now caused by compromised third-party vendors, cybersecurity programs are quickly evolving towards a greater emphasis on Vendor Risk Management.
For advice on choosing the best VRM solution for your specific data breach mitigation requirements, read on.
The Risks of Not Having a Vendor Risk Management Solution
According to the 2023 Cost of a Data Breach report by IBM and the Ponemon Institute, data breach damage costs have peaked (again) at USD 4.45 million. Data breaches involving compromised third-party vendors increased this amount by about $216,441.

Vendor Risk Management is a cybersecurity program ensuring vendor security risks do not exceed your risk appetite.
A Vendor Risk Management platform helps security teams achieve confident control over their third-party attack surface, ensuring vendor risks are detected and remediated before cybercriminals exploit them. The impact of a VRM tool goes beyond reduced data breach damage costs. A resilient Vendor Risk Management program could significantly reduce your risk of a data breach.
According to the Verizon 2022 Data Breach Investigations Report, 62% of all data breaches happen via third-party vendors.
To provide the most accurate measure of performance, this list compares VRM solutions against a minimal set of features required to contend with today's third-party cyber threat landscape.
What are the features of the best Vendor Risk Management solutions?
Your choice of Vendor Risk Management software should offer the following set of features as a minimum:
- Attack Surface Monitoring - Real-time risk monitoring for vendor vulnerabilities that could facilitate security incidents. Attack Surface Monitoring also feeds into a broader cybersecurity discipline known as Attack Surface Management, which helps you maintain a minimal digital footprint to further decrease data breach risks.
- Vendor Risk Assessment Management - The risk assessment lifecycle comprises multiple stages, from due diligence to evidence gathering, risk monitoring, etc. Ideally, all stages of this lifecycle should be addressed in the one cloud-based VRM platform.
- Security Questionnaire Automation - If not streamlined to optimal efficiency and scalability, clunky security questionnaire processes cause disruptions across all dependent stages of the VRM lifecycle, especially risk assessments.
- Risk Remediation Workflows - A complete risk remediation workflow must be included in a VRM platform so that discovered risks can be instantly addressed.
- Regulatory Compliance Tracking - Regulatory violations bring significant penalties. Since the security postures of service providers in the supply chain directly impact compliance efforts, a VRM platform should include vendor risk and compliance tracking features.
- Vendor Security Posture Tracking - Security posture quantification tools, like security ratings, allow each vendor’s degree of data breach susceptibility to be tracked in real time. This feature is an invaluable aid when managing a substantial vendor attack surface.
- Cybersecurity Reporting Workflows - With stakeholders expecting greater visibility into your cybersecurity program’s performance, A VRM platform should include a feature for instantly generating reports pulling relevant data about your VRM efforts.
Essential Vendor Risk Management software metrics
Each solution in this list will also be measured against the following performance metrics:
- User-Friendliness - A user-friendly VRM platform streamlines onboarding, allowing your organization to benefit from the platform’s functionality as quickly as possible
- Customer support - An ever-present customer support team will give you the peace of mind of knowing any administrative and troubleshooting queries will be addressed quickly, allowing you to focus entirely on drawing value from the VRM tool.
- Risk Scoring Accuracy - The efficiency of a VRM program is directly tied to the accuracy of its risk-scoring mechanisms. Risk scores inflating vendor risk profiles with superfluous threats cause unnecessary strain on remediation resources. Alternatively, risk-scoring mechanisms missing important threats leave an organization unknowingly exposed to critical data breach risks.
11 Best Vendor Risk Management tools in 2024
The top eleven Vendor Risk Management tools options for improving VRM program efficiency are listed below.
1. UpGuard
Ideal for organizations looking for a comprehensive Vendor Risk Management tool addressing the full scope of the VRM lifecycle, including instant vendor-security risk insights, regulatory compliance tracking, 360-degree risk assessments, and automated workflows.
UpGuard’s performance against Key Vendor Risk Management features
Below is an overview of how UpGuard performs against the seven key features of an ideal Vendor Risk Management product.
(i). Attack Surface Monitoring
The UpGuard platform includes attack surface monitoring features addressing internal and complete third-party attack surfaces. Integrating with UpGuard’s Attack Surface Management module, this continuous monitoring feature discovers emerging supplier risks and vulnerabilities across vendor relationships, helping security teams achieve confident control of their vendor attack surface. UpGuard’s attack surface monitoring scope extends to the fourth-party landscape, empowering users to address potential data breach risks extending as afar as the fouth-party attack surface.
For an overview of UpGuard’s attack surface monitoring capabilities in the context of attack surface management, watch this video:
(ii). Vendor Risk Assessment Management
UpGuard’s VRM SaaS tool streamlines the end-to-end vendor risk assessment process, removing all dependence on frustrating spreadsheets. The vendor risk assessment lifecycle stages addressed inside the UpGuard platform include:
- Evidence Gathering - Gathering evidence to form a complete picture of inherent risks before vendor onboarding or initial risk exposure for existing vendors. This data can either be gathered from trust and security pages, certifications, or questionnaire responses.
- Risk Management - The process of deciding which risks to accept, waive, and prioritize in remediation efforts. All risks are ranked by level of criticality following risk identification.
Watch this video for an overview of UpGuard’’s risk assessment workflow.
Learn more about UpGuard’s risk assessment features >
(iii). Security Questionnaire Automation
To address the most common cause of VRM process inefficiency - delayed questionnaire submissions, UpGuard has introduced automation technology to revolutionize the vendor questionnaire process.
- AI Autofill - This feature auto-populates suggested questionnaire responses based on a database of a vendor’s previously submitted questionnaires.
- AI Enhance - This feature allows vendors to produce clear and concise questionnaire responses from a set of bullet points.
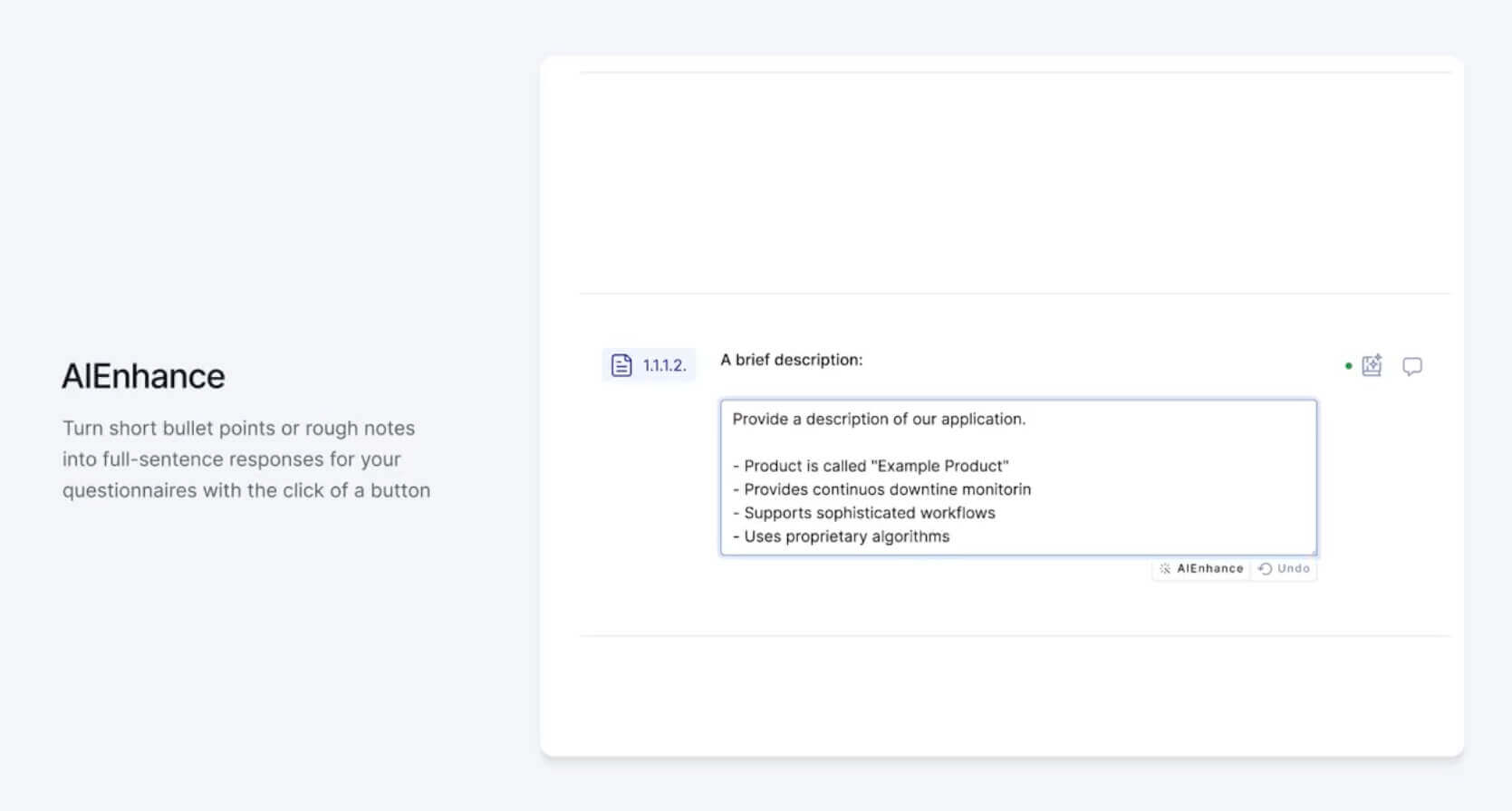

UpGuard’s vendor questionnaire automation features significantly reduce time spent completing questionnaires, which means you receive responses in hours, instead of days (or weeks).
Watch this video for an overview of these features in UpGuard’s AI Toolkit.
UpGuard’s AI-powered features are available across all of its pre-built vendor questionnaire templates, which map to popular frameworks and standards, including HIPAA, PCI DSS, and ISO 27001.
Learn more about UpGuard’s questionnaires >
(iv). Risk Remediation Workflows
UpGuard includes an in-built risk remediation workflow for instantly addressing risks identified in risk assessments and questionnaires. To help security teams prioritize remediation tasks that will have the greatest positive impacts on an organization's security posture, UpGuard projects the likely security posture improvements for selected remediation tasks.

Watch this video for an overview of UpGuard’s risk remediation workflow.
(v). Regulatory Compliance Tracking
UpGuard’s VRM solution tracks each vendor’s degree of alignment against popular regulations based on security questionnaire responses.
UpGuard’s security questionnaires map to the standards of regulations like HIPAA, PCI DSS, and NIST 800-53, identifying compliance risks based on questionnaire responses. This feature offers a competitive advantage to VRM and Third-Party Risk Management programs, simplifying compliance management, even during the most critical phases of a vendor relationship.- onboarding and offboarding.
Watch this video for an overview of how UpGuard’s compliance tracking feature can also track alignment with cybersecurity framework standards.
To expedite remediation processes, UpGuard offers vendor collaboration features, streamlining communication about specific security risk fixes.
Watch this video to learn how UpGuard streamlines vendor collaborations to achieve optimum remediation efficiently.
(vi). Vendor Security Posture Tracking
UpGuard’s security rating feature quantifies vendor security postures by evaluating over 70 critical attack vectors across six risk categories.
- Network Security
- Phishing and Malware
- Email Security
- Brand and Reputation
- Website Security
- Questionnaire Risks
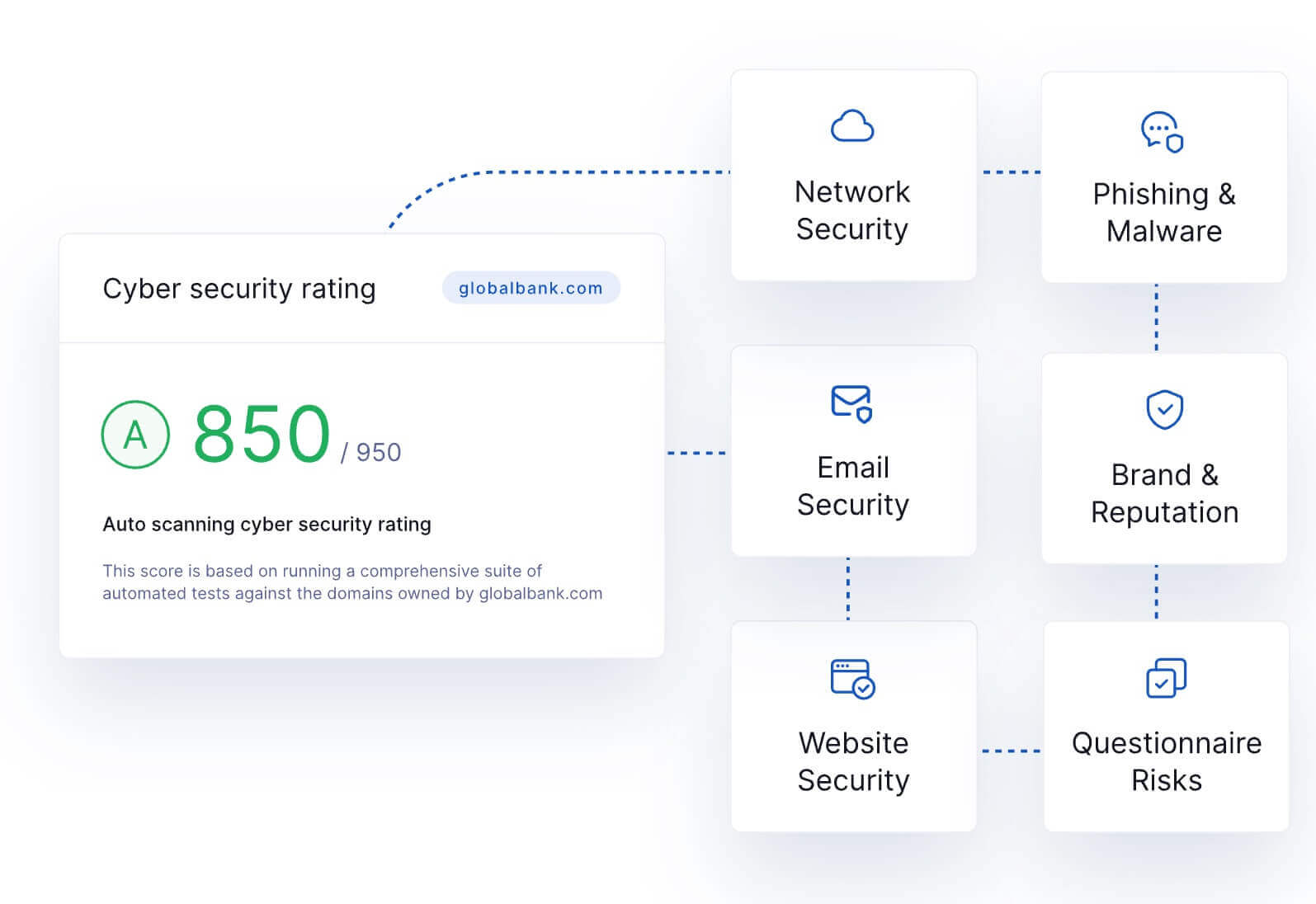
This risk category list represents the most concise supply chain security risk profile leading to third-party breaches. While considering more attack vector categories might seem like it would produce more accurate security posture calculations, doing so increases the likelihood of including vanity factors not truly indicative of actual security risks - which will only frustrate your security teams.
Final quantified security postures are represented as a numerical value ranging from 0-950.
UpGuard’s vendor risk ratings mechanism adheres to the Principles for Fair and Accurate Security Ratings to produce objective security posture measurements that can be independently verified.
Learn more about UpGuard’s security ratings >
(vii). Cybersecurity Reporting Workflows
UpGuard’s Vendor Risk Management platform offers a library of customizable cybersecurity reporting templates showcasing vendor risk mitigation efforts and the performance of other risk management processes to keep stakeholders informed of your VRM performance.
To streamline the complete reporting workflow, UpGuard allows board reports to be exported into editable PowerPoint slides, relieving the burden of preparing for VRM and TPRM board presentations.

Learn more about UpGuard’s reporting and dashboard features >
UpGuard’s performance against key Vendor Risk Management metrics
Below is an overview of how UpGuard performs against three primary performance metrics collectively representing the usability and reliability of a VRM tool.
(i). User Friendliness
UpGuard’s intuitive and user-friendly design is commonly highlighted in customer reviews on Gartner and G2.
"Powerful and deep insights into external risk posture Simple and intuitive user interface. Great support."
- 2023 Gartner review
"I really value how simple it is to install and operate UpGuard. The program offers a complete cybersecurity answer and has an intuitive user interface."
- 2023 G2 review
Download UpGuard’s G2 report >
To get a sense of how quickly the onboarding process is with UpGuard, 7 Chord, an independent provider of predictive pricing and analytics to fixed-income traders, was able to onboard over 20 of its vendors and start monitoring them immediately in less than 30 minutes.
"We found UpGuard’s design very clean and very intuitive – more intuitive than the UI of its competitors, making it an easy decision to go with UpGuard."
- 7 Chord
(ii). Customer Support
UpGuard strives to offer the best levels of customer support in the industry. Independent reviews verify that UpGuard is meeting this objective.
“Our account manager is always responsive when we have questions, and support provides a response within 24 hours each time.”
- 2023 Gartner review (read review)
“UpGuard offers the best support after onboarding. UpGuards CSM representatives are very professional & prompt in responding to the issues raised. Tech support is also great.”
- 2023 G2 review (read review)
(iii). Risk Scoring Accuracy
UpGuard’s risk-scoring mechanisms aim to reflect the most objectively accurate profile of a vendor’s security posture. UpGuard’s vendor risk profile offers a detailed breakdown of all risks influencing security posture measurements represented as security ratings.
The detail of discovered risks and the ability to instantly request remediations for each risk offer opportunities to independently confirm the legitimacy of each security threat and the accuracy of its criticality ratings.

UpGuard’s risk scoring accuracy has been highlighted in independent user reviews.
"UpGuard offers the most up-to-date and accurate information about third parties. Its third-party monitoring capability is handy for most medium to large enterprises."
2023 G2 review (read review)
2. SecurityScorecard
Ideal for businesses needing detailed risk assessments and strong visualization capabilities.
SecurityScorecard’s performance against key Vendor Risk Management features
Below is an overview of how SecurityScorecard performs against the seven key features of an ideal Vendor Risk Management product.
See how UpGuard compares with SecurityScorecard >
(i). Attack Surface Monitoring
SecurityScorecard offers an attack surface monitoring feature that can identify internal and third-party security risks by scanning public-facing attack vectors.
Some of the indicators of risk considered by SecuityScorecard’s attack surface scanning tool include:
- Open ports
- DNS
- HSTS
- SSL

Most of SecurityScorecard’s risk checks are refreshed at a weekly rate. Compared with the UpGuard platform, which completes its non-intrusive scans of IPv4 web space in just 24 hours, this is a significant delay that could lead to inaccurate security rating calculations.
See how UpGuard compares with SecurityScorecard >
(ii). Vendor Risk Assessment Management
SecurityScorecard offers a Vendor Risk Assessment workflow through Atlas - a vendor questionnaire and evidence exchange platform for establishing vendor risk profiles. However, because vendor risk monitoring and questionnaire automation modules are offered as separate licenses, data sharing between vendor risk assessment phases isn't streamlined, which could impact the quality of holistic vendor risk views and calculations.
This isn't a minor issue. Disjointed vendor risk data sharing between risk assessment modules makes it difficult for users to understand what a vendor's total actual risk is, which undermines the ultimate purpose of a VRM tool - to improve the efficiency of your VRM program.
UpGuard streamlines the entire vendor risk assessment workflow with fully integrated features, ensuring holistic vendor risk visibility and accuracy is always maintained.

(iii). Security Questionnaire Automation
SecurityScorecard applies automation technology to its vendor questionnaire processes to expedite response times. One way this is achieved is by suggesting responses based on previously submitted questionnaires.
SecurityScorecard’s application of automation technology could reduce vendor questionnaire completion times by 83%.
SecurityScorecard offers a vendor questionnaire management module with a library of questionnaire mapping to popular regulations and standards.
(v). Regulatory Compliance Tracking
SecurityScorecard includes a vendor collaboration feature, making it easier for security teams and impacted vendors to work together to address compliance risks. By combining security rating data with questionnaire data, SSC can discover emerging compliance risks even between official assessment schedules.

(iv). Risk Remediation Workflows
SecurityScorecard offers managed remediation services following a data breach, an offering made possible by its acquisition of LIFARS, a global leader in digital forensics, incident response, ransomware mitigation, and cyber resiliency services.
SSC also gives users the option of managing risk remediations, either by submitting resolution requests or by providing details of compensating controls that are in place.
Like UpGuard, SecurityScorecard also projects the impact of selected remediation tasks on a company’s security posture.

However, SecurityScorecard doesn’t offer its risk remediation feature within a fully integrated Vendor Risk Management workflow, which could impede the scalability of your VRM program.
UpGuard, on the other hand, streamlines the entire Cyber Vendor Risk Management lifecycle in a single platform, integrating multiple VRM processes, including:
- Initial onboarding
- Risk assessments and security approval for new vendors
- Ongoing risk monitoring & remediation
- Annual vendor risk and review
UpGuard is one of the few VRM product options addressing the complete end-to-end Vendor Risk Management lifecycle.
(vi). Vendor Security Posture Tracking
SecurityScorecard tracks vendor security postures with a security rating feature evaluating cyber risks across ten risk factors:
- Network Security
- DNS Health
- Patching Cadence
- Endpoint Security
- IP Reputation
- Application Security
- Cubit Score
- Hacker Chatter
- Information Leak
- Social Engineering
Final quantified security postures are represented as a letter grade ranging from A to F.

(vii). Cybersecurity Reporting Workflows
SecurityScorecard includes a cyber report generation feature that instantly pulls relevant vendor risk data and produces in-depth board reports. SSC’s reports are customizable, showcasing risk trends in your vendor ecosystem and benchmark your VRM performance against industry averages.

SecurityScorecard’s performance against key Vendor Risk Management metrics
Below is an overview of how SecurityScorecard performs against three primary performance metrics collectively representing the usability and reliability of a VRM tool.
(i). User Friendliness
While SecurityScorecard’s dashboard is informative, some users find it a little too overwhelming and unintuitive. Poor user-friendliness could slow implementation timelines and delay investment returns.
“The tool was not as user-friendly as its competitors. It’s for more tech-heavy users. This tool isn't ideal for collaboration with other business units such as legal/contract mgmt.”
- G2 review (read review)
(ii). Customer Support
According to independent reviews, SecurityScorecard’s support team has demonstrated prompt responsiveness to user issues.
"SS has a responsive support team. which is critical to me on time-sensitive projects."
- G2 review (read review)
(iii). Risk Scoring Accuracy
How Accurate are SecurityScorecard’s Risk Ratings?
According to reviews on Gartner and G2, SecurityScorecard has been found to produce false positives, which could impact the accuracy of its security rating calculations and, therefore, the overall efficiency of your Vendor Risk Management program.
“According to third-party feedback, unfortunately, it gives many false positives.”
- G2 review (read review)
“Seems like there might be some false positives. Also, limited details on risk details.”
- Gartner review (read review)
“Not finding the correct security issues, More spamming, need to get consent before adding the other domain even though it is light scan.”
- Gartner review (read review)
3. Bitsight
Ideal for enterprises requiring a risk-based TPRM tool with extensive vendor profiling.
Bisight’s performance against key Vendor Risk Management platform features
Below is an overview of how BitSight performs against the seven key features of an ideal Vendor Risk Management product.
(i). Attack Surface Monitoring
Bitsight pulls attack surface insights from multiple sources (cloud, geographies, subsidiaries, and your remote workforce) into a single dashboard.
Bitsight monitors both the internal and external attack surfaces to help security teams:
- Visualize critical vendor risks
- Discover shadow IT
- Reduce corporate digital footprints to support enterprise risk management
- Monitor cyber risks in cloud infrastructures
See how UpGuard compares with Bitsight >
(ii). Vendor Risk Assessment Management
Bitsight has developed a vendor risk assessment module that can conform to the unique vendor risk profile. This capability offers a more targeted approach to vendor risk assessments than the broad, one-size-fits-all approach that characterizes ineffective vendor risk assessment platforms.
(iii). Security Questionnaire Automation
Bitsight keeps a comprehensive record of historic vendor risk assessment data for a detailed representation of vendor risk performance trends. Following its partnership with Third Party Trust, Bitsight now offers vendor security questionnaire review workflow as part of a broader third-party risk management solution. These questionnaires map popular industry standards, such as NIST, ISO, CIS Controls, and Shared Assessments.
(iv). Risk Remediation Workflows
Bitsight claims to support the complete Vendor Risk Management lifecycle, which is inclusive of a risk remediation workflow. Users can track whether remediation requests have been opened, resolved, accepted, or are in progress.

Bitsight users have noticed that remediated security risks take far too long to be removed from cyber risk reports, which could result in an inaccurate depiction of your overall. security posture.
"The time for us to remediate is a lot quicker, and I don't believe we should have to wait the 60 days it takes for them to remove it from the report. The response back from support on some of the issues we face is very canned and doesn’t really provide insight."
- Gartner review (read review)
"Configuration issues that are fixed stay on record for 60 days, and I have not determined that the product recognizes that the issue is resolved by changing status in any way."
- Gartner review (read review)
(v). Regulatory Compliance Tracking
Bitsight doesn’t have a single published source listing all of the regulations it supports compliance with. Some blog posts allude to regulation and cyber frameworks that Bitsight could support, such as NIS 2 and SOC 2, but this messaging isn’t very clear.
When investing in a VRM solution, it’s important to have complete confidence in its ability to address regulatory compliance risks - a critical risk factor influencing your security posture.
According to Gartner, Regulatory compliance tracking is a critical capability of IT Vendor Risk Management solutions. As such, to encourage trust in its effectiveness, a VRM solution should clearly highlight its regulatory compliance capabilities.

(vi). Vendor Security Posture Tracking
Bitsight’s external attack surface monitoring features aim to represent your vendor’s attack surface as an attacker would see it - by highlighting the vendor’s most vulnerable to data breach attempts.
Bitsight quantifies security postures as a numerical value rating from 0-820. To help you determine whether your vendor risk exposure is on an upward or downward trend, Bitsight keeps 12 months of security rating data for each vendor.
(vii). Cybersecurity Reporting Workflows
Bitsight’s Executive Reporting feature pulls relevant vendor risk metrics into a cybersecurity report for board meetings. A particularly helpful feature in Bitsights’s reporting workflow is the inclusion of Cyber Risk Quantification - an approximation of the financial impact of selected cyber threat scenarios. CRQ is a beneficial tool for making intelligence cybersecurity investment decisions.

Learn how UpGuard helps financial services prevent data breaches >
Bitsight’s performance against key Vendor Risk Management metrics
Below is an overview of how Bitsight performs against three primary performance metrics collectively representing the usability and reliability of a VRM tool.
(i). User Friendliness
The Bitsight platform isn’t intuitive, so implementation may take longer than expected. A red flag for a potentially steep learning curve in a VRM solution is the expectation of training videos. Ideally, the UX of a VRM tool should be so intuitive users naturally begin understanding how to navigate it without the support of training videos.
“Training is lacking. No videos.”
- 2023 Gartner review (read review)
(ii). Customer Support
Bitsight users have reported excellent support from the customer support team.
"Customer service was excellent, everything was explained well, all my questions were answered soundly."
- G2 review (read review)
(iii). Risk Scoring Accuracy
How Accurate are Bitsight’s Risk Ratings?
Bitsight’s excessive delays in reflecting the impact of remediated security risks could be a significant frustration for security teams basing their VRM decisions on data not reflective of the actual vendor attack surface.
UpGuard, on the other hand, scans and refreshes risks daily for each vendor to ensure security teams always operate from the most up-to-date and accurate vendor risk data.
4. OneTrust
Ideal for SMBs focusing on automating vendor risk assessments and improving regulatory compliance.
OneTrust’s performance against key Vendor Risk Management software features
Below is an overview of how OneTrust performs against the seven key features of an ideal Vendor Risk Management product.
- Attack Surface Monitoring: OneTrust’s Data Discovery product helps you track sensitive data flows to minimize your sensitive data footprint
- Vendor Risk Assessment Management: The platform maps to the primary stages of the VRM lifecycle, including due diligence and continuous monitoring.
- Security Questionnaire Automation: OneTrust streamlines security questionnaire workflows with questionnaire templates mapping to popular standards. Questionnaire can be adapted based on a vendor’s previous responses.
- Risk Remediation Workflows: OneTrust provides out-of-the-box remediation suggestions for all third-party vendors added to a centralized inventory, streamlining remediation workflows from the first instance of importing.
- Regulatory Compliance Tracking: With qustionnaire templates mapping to popular regulatory standards, OneTrust identifies compliance-related risks across all assessed vendors.
- Vendor Security Posture Tracking: OneTrust leveraged security rating technology to track security posture deviation across all monitored vendors.
- Cybersecurity Reporting Workflows: OneTrust includes a cybersecurity report generation feature to keep stakeholders informed of vendor risk management efforts.
OneTrust’s performance against key Vendor Risk Management metrics
Below is an overview of how OneTrust performs against three primary performance metrics collectively representing the usability and reliability of a VRM tool.
- User-Friendliness: OneTrust’s platform is user-friendly and easy to navigate, facilitating quick VRM program implementation.
"Overall, the product is decent, and the module costs are pretty affordable. The product is highly customizable but certainly requires getting to know it and use it and may require feedback from OneTrust support."
- 2022 Gartner Review
- Customer Support: OneTrust supports its users with a fast and reliable customer support team.
"The customer support is very well as prompt reply for any ongoing issues. We tried integrating it with our in house hosted tools for better management."
- 2023 G2 Review
- Risk Scoring Accuracy: OneTrust’s risk-scoring mechanisms offer a delayed representation of the true state of an organization’s external attack surface, which could have a significant impact on risk-scoring accuracy.
5. Prevalent
Ideal for organizations needing a flexible hybrid approach to VRM.
Prevalent’s performance against key Vendor Risk Management features
Below is an overview of how Prevalent performs against the seven key features of an ideal Vendor Risk Management product.
- Attack Surface Monitoring: Prevalent offers comprehensive real-time monitoring for vulnerabilities and vendor-related security risks through its Global Vendor Intelligence Network. The platform’s scope of third-party attack vector monitoring extends to dark web forums and risk intelligence feeds to support information security and data privacy standards.
- Vendor Risk Assessment Management: The platform supports the entire vendor assessment lifecycle, including due diligence, continuous monitoring, and remediation. Prevalent provides pre-built, customizable assessment templates aligned with industry standards like GDPR, SOC 2, and PCI DSS. The platform also includes an exchange for sharing completed vendor risk reports, streamlining the due diligence process.
- Security Questionnaire Automation: Prevalent tracks the distribution of vendor security questionnaires, ensuring potential risks of third-party relationships undergo ongoing monitoring with point-in-time assessments. Notifications are triggered via automated reminders to encourage timely questionnaire completions.
- Risk Remediation Workflows: Prelavent includes a vendor risk remediation workflow integrates into its risk assessment module to seamlessly progress detected risks through the management lifecycle. The platform also supports users with guidance on corrective actions.
- Regulatory Compliance Tracking: Prevalent’s questionnaires map to regulatory standards and frameworks to discover areas of misalignment. Compliance evidence can be exported into compliance reports to support audits and regulatory reviews.
- Vendor Security Posture Tracking: Prevalent uses security ratings to quantify and monitor the security posture of vendors. These security ratings consider historical data breaches among other vendor risk factors.
- Cybersecurity Reporting Workflows: Prevalent offers customizable cybersecurity reporting templates pulling VRM insights from the platform for stakeholders
Prevalent’s performance against key Vendor Risk Management metrics
Below is an overview of how Prevalent performs against three primary performance metrics collectively representing the usability and reliability of a VRM tool.
- User-Friendliness: Prevalent has a fast and intuitive implementation workflow. However, it may take longer than expected to learn how to navigate its VRM features efficiently.
- Customer Support: Prevalent is praised for its excellent customer support during onboarding and beyond.
"My experience with Prevalent has been very positive. The company has been very hands-on with us, from our onboarding to the biweekly/monthly cadence calls to our support questions and beyond. It feels like the company is focused on growing their services with their clients, which is a huge plus. As expected, there are hiccups in the system every now and then, but the support staff is always willing to assist and help diagnose the issues."
- 2023 Gartner Review
- Risk Scoring Accuracy: Prevalent’s lack of transparency about the number of compares included within its scanning range is a potential indication of the questionable accuracy of its vendor risk-scoring capabilities.
"I wish the dashboard was customizable so I could see the data I want upon logging in. I also wish the reporting was more accurate to only show active vendors versus disabled ones."
- 2021 G2 Review
6. Panorays
Ideal for businesses seeking in-depth third-party risk management and monitoring.
Panorays’ performance against key Vendor Risk Management software features
Below is an overview of how Panorays performs against the seven key features of an ideal Vendor Risk Management product.
- Attack Surface Monitoring: Panorays leverages its Risk DNA technology to quantify risk scores based on various attack factors. The platform also addressed the external attack surface to offer visibility into third-party digital footprints.
- Vendor Risk Assessment Management: The Panorays platform includes features supporting all stages of the VRM lifecycle, from onboarding to continuous monitoring.
- Security Questionnaire Automation: Panorays leverages AI technology to scan previous questionnaire responses and supporting documentation, such as certifications, to expedite questionnaire completions.
- Risk Remediation Workflows: The platform integrates with third-party workflow apps like ServiceNow and RSA to streamline remediation workflows.
- Regulatory Compliance Tracking: Panorays tracks compliance risks with its library of questionnaires mapping to the popular regulatory standards. Tailored assessments can also be created based on unique compliance risk contexts with the platform’s Risk DNA feature.
- Vendor Security Posture Tracking: Panorays quantifies vendor security postures with security ratings for real-time tracking of vendor security posture deviations.
- Cybersecurity Reporting Workflows: Panorays offers customization templates for generating cybersecurity reports overviewing VRM performance for stakeholders and board members.
Panorays’ performance against key Vendor Risk Management metrics
Below is an overview of how Panorays performs against three primary performance metrics collectively representing the usability and reliability of a VRM tool.
- User-Friendliness: The Panorays platform is quick to implement and designed to be user-friendly.
"Easy to use and set up, the dashboards are pretty intuitive."
- 2022 Gartner Review
- Customer Support: Users report a reliable customer support base for Panorays. However, without pricing transparency on its website. Prospects are forced to interact with sales team members, which may not be a desired level of support at such an early stage of the prospective process.
- Risk Scoring Accuracy: Panorays considers a limited scope of third-party data leakage in its risk scoring methodology, which could limit the accuracy of final scoring values.
7. RiskRecon
Ideal for enterprises seeking deep, actionable insights into the cybersecurity health of external partners.
RiskRecon’s performance against key Vendor Risk Management software features
Below is an overview of how RiskRecon performs against the seven key features of an ideal Vendor Risk Management product.
- Attack Surface Monitoring: RiskRecon offers real-time monioring of vendor vulnerabilities in an organization’s attack surface. The likelihood of vendors suffering a security incident such as a data breach is quantified by considering 11 security domains and 41 attack vector factors.
- Vendor Risk Assessment Management: RiskRecon supports the onboarding and continuous monitoring phases of the VRM lifecycle, but it does not provide vendor risk assessment workflows.
- Security Questionnaire Automation: RiskRecon does not offer an inbuilt security questionnaire workflow, which is a significant concern given the criticality of this phase in the VRM lifecycle. To fill this gap, RIskRecon is forced to partner with other solutions offering a risk assessment solution, which unnecessarily bloats the digital footprint and, therefore, the attack surface of this VRM tool.
- Risk Remediation Workflows: The platform has a very limited remediation workflow. not accommodating for collaboration between multiple parties. Without a seamless process for inviting parties to collaborate with specific remediation processes, the limitations of RIskRecon’s remediation workflow impacts the scalability of a VRM program being supported by the tool.
- Regulatory Compliance Tracking: Through its compliance indicators feature, RiskRecon can measure alignment against popular regulatory standards and cyber frameworks. However, the platform does not offer a degree of compliance effort visibility expected by compliance teams.
- Vendor Security Posture Tracking: RiskRecon uses security ratings to quantify and monitor vendor security postures.
- Cybersecurity Reporting Workflows: RiskRecon includes a cyber risk report generation feature that summarises an organization’s security posture based on external security risk factors.
RiskRecon’s performance against key Vendor Risk Management metrics
Below is an overview of how RiskRecon performs against three primary performance metrics collectively representing the usability and reliability of a VRM tool.
- User-Friendliness: Users are reportedly disappointed with RiskRecon’s ability to adapt to the ever-changing requirements of Vendor Risk Management.
"Integration with other GRC tools and risk platforms was oversold and not as mature as we were led to believe. RSA integration was not smooth, and there were several bumps along the way that we had to escalate to executive leadership."
- 2022 Gartner Review
"They exclusively focus on cyber security data. As with all players in this space, they too misidentify assets on occasion. Innovation on core product has slowed just a bit since joining MasterCard."
- 2022 Gartner Review
- Customer Support: RiskRecon's website does not disclose its pricing, forcing prospects to engage with sales support staff only to learn that the pricing is outside of their budget.
"RiskRecon has some issues with integration and is also a costly tool."
- 2022 Gartner Review
- Risk Scoring Accuracy: Users have reported that RiskRecon relies on legacy data to build its VRM insights. This is very concerning as it causes cybersecurity staff to base their vendor risk management strategies on a false outlook of external risk exposure.
"Some reporting functions create false positives which require correspondence with the vendor to tune the accuracy of the reporting function."
- 2022 Gartner Review
"Legacy data; updates can be delayed, and modifications are difficult."
- 2022 Gartner Review
8. ProcessUnity
Ideal for businesses wanting to reduce the busy work involved in due diligence.
ProcessUnity’s performance against key Vendor Risk Management software features
Below is an overview of how ProcessUnity performs against the seven key features of an ideal Vendor Risk Management product.
- Attack Surface Monitoring: ProcessUnity offers continuous monitoring of external inherent risks, quantifying vendor security postures as security ratings.
- Vendor Risk Assessment Management: The platform emphasizes supporting the due diligence phases of vendor onboarding, particularly pre- and post-contract due diligence. A more streamlined and secure due diligence workflow encourages efficiency in the downstream risk assessment process.
- Security Questionnaire Automation: ProcessUnity offers a risk assessment library mapping to popular regulations and standards. By leveraging AI technology in its Predictive Risk Insights feature, ProcessUnity could expedite risk discovery through questionniares efforts.
- Risk Remediation Workflows: The platform leverages AI technology to streamline third-party risk discovery and remediation through its Predictive Risk Insights feature.
- Regulatory Compliance Tracking: ProcessUnity primarily focuses on tracking compliance risks associated with the Digital Operational Resilience Act (DORA) and the German Supply Chain Act (LkSG).
- Vendor Security Posture Tracking: The platform offers a security rating features to expedite the process of vetting potential vendor within the due diligence phase of VRM.
- Cybersecurity Reporting Workflows: ProcessUnity offers a configurable cyber reporting template for tailoring VRM reports to the visibility requirements of stakeholders.
ProcessUnity’s performance against key Vendor Risk Management metrics
Below is an overview of how ProcessUnity performs against three primary performance metrics collectively representing the usability and reliability of a VRM tool.
- User-Friendliness: Users are reportedly the product as being quick to implement and easy to navigate.
Extremely easy to deploy. A lot of graphs to help data interpretation at a glance. Good user interface."
- 2022 Gartner Review
- Customer Support: ProcessUnity users have reported very slow customer support efforts, especially when seeking to address queries about features critical to a VRM program, such as vendor risk assessment processes.
"As an end user, it is not clear when I have a task to complete or if an assessment needs to be updated. Contacting CyberGRX for assistance is very slow, and often the links in their emails do not work, which requires additional communication."
- 2024 Gartner Review
- Risk Scoring Accuracy: The platforms seem to pull detailed insights about vendor security risks to produce reliable risk-scoring values.
9. Vanta
Ideal for small businesses needing to simplify vendor compliance tracking
Vanta’s performance against key Vendor Risk Management solution features
Below is an overview of how Vanta performs against the seven key features of an ideal Vendor Risk Management product.
- Attack Surface Monitoring: Vanta offers a continuous monitoring solution based on tracking alignment against security and regulatory standards. However, the platform offers very limited coverage of the external attack surface in its monitoring scope.
- Vendor Risk Assessment Management: Vanta automatically assigns an inherent risk score for all onboarded members to expedite progression through risk assessment workflows. The tool bases its risk assessment approach on the guidelines of ISO 27005 risk, helping users meet the standards of ISO 27001, SOC 2, and HIPAA.
- Security Questionnaire Automation: Vanta automates manual, repetitive questionnaire tasks, such as the completion of repetitive questionnaires.
- Risk Remediation Workflows: Through its risk management solution, Vanta integrates remediation workflows into its risk assessment feature to expedite vendor risk management.
- Regulatory Compliance Tracking: Vanta tracks compliance against all of the popular cybersecurity frameworks and regulations.
- Vendor Security Posture Tracking: Vanta does not incorporate vendor security ratings or vendor data leaks into risk assessment and remediation insights.
- Cybersecurity Reporting Workflows: The platform allows compliance reports to be generated through its Trust Report feature.
Vanta’s performance against key Vendor Risk Management metrics
Below is an overview of how Vanta performs against three primary performance metrics collectively representing the usability and reliability of a VRM tool.
- User-Friendliness: Vanta is known for its user-friendly interface and intuitive compliance tracking workflows.
"We have been using Vanta for over a year, and it has helped us achieve SOC2, HIPAA, and ISO 27001 certification. Vanta is a trusted partner for our security and compliance."
- 2024 Gartner Review
- Customer Support: Overall, users are pleased with the platform’s customer support offering but disappointed with its lack of live chat availability.
It's worth noting that most issues with Vanta can require multiple updates on support tickets. While the support team is very responsive and professional, addressing certain issues can sometimes be time-consuming with a lack of live chat or phone support options. To date, most of my correspondence has been through email, which can cause long delays between different timezones."
- 2024 G2 Review
- Risk Scoring Accuracy: The trustworthiness of Vanta’s risk scoring calculations is questionable, given its limited consideration of the external attack surface.
10. Drata
Ideal for organizations needing to streamline compliance workflows and maintain audit readiness.
Drata’s performance against key Vendor Risk Management solution features
Below is an overview of how Vanta performs against the seven key features of an ideal Vendor Risk Management product.
Learn how UpGuard compares with Drata >
- Attack Surface Monitoring: Drata helps organizations achieve audit readiness by monitoring compliance-related risks. However, the solution lacks an inventory discovery feature, which is a critical component of Attack Surface Management.
For an overview of Attack Surface Management and its key processes, watch this video.
- Vendor Risk Assessment Management: The platform offers a policy builder to simplify compliance risk tracking in its assessment workflow.
- Security Questionnaire Automation: Through its Trust Center, Drata expedites the vendor security profile building, streamlining the questionnaire workflows that follow
- Risk Remediation Workflows: Drata streamlines risk management by automatically mapping discovered risks to their corresponding risk controls. Users can also opt to receive alerts about evolving risks related to their tailored treatment plans.
- Regulatory Compliance Tracking: Drata tracks compliance gaps against 14 popular cybersecurity standards.
- Vendor Security Posture Tracking: Drata tracks vendor security postures using qualitative methods, a subjective indication of vendor risk severity through a graphical risk posture bar. This approach makes it difficult to align multiple parties with risk management strategies due to its subjective nature. A more objective approach to security posture tracking that multiple parties are more comfortable aligning with, including stakeholders, is the use of security ratings.

- Cybersecurity Reporting Workflows: The platform allows security posture reports to be generated for stakeholders and board members to communicate cyber risk exposures at any time.
Drata’s performance against key Vendor Risk Management metrics
Below is an overview of how Vanta performs against three primary performance metrics that collectively represent the usability and reliability of a VRM tool.
- User-Friendliness: Drata is known for its user-friendly interface, facilitating quick onboarding and efficient use.
- Customer Support: Users are reportedly very pleased with Drata’s customer support.
Great product, helping our company align with the ISO 27001 security framework. The support via the chat is outstanding and responsive."
- 2024 Gartner Review
- Risk Scoring Accuracy: Drata’s lack of asset discovery functionality could limit the platform's ability to consider the impact of asset risk on vendor risk scores, making the accuracy of its risk-scoring methodology questionable.
11. Black Kite
Ideal for dynamic risk rating, open-source threat intelligence, non-intrusive cyber reconnaissance, and detailed reporting.
Black Kite’s performance against key Vendor Risk Management features
Below is an overview of how Vanta performs against the seven key features of an ideal Vendor Risk Management product.
Learn how UpGuard compares with Black Kite >
- Attack Surface Monitoring: Black Kite covers a comprehensive scope of the third-party attack surface build its risk insights. Some of the risk domains covered include set reputation, credential compromises, social media monitoring, and dark web searches.
- Vendor Risk Assessment Management: Black Kite does not offer an inbuilt risk assessment workflow. Users would need to integrate separate third-party risk management software to build a complete vendor risk assessment program.
- Security Questionnaire Automation: Black Kite uses AI technology to parse completed questionnaires and other relevant cybersecurity documentation to calculate compliance and risk exposure scores for each vendor.
- Risk Remediation Workflows: The compliance risks detected through the platform’s AI-powered document parsing capabilities expedite risk discovery and subsequent remediation tasks. However, the platform primarily focuses on the remediation and management of compliance-related risks.
- Regulatory Compliance Tracking: With its cyber-aware AI, Black Kite can parse multiple document types, not just questionnaire responses, to build a comprehensive compliance risk exposure profile. Detected risks are automatically mapped to popular frameworks, including SOC 2, NIST, GDPR, and ISO27001,
- Vendor Security Posture Tracking: Black Kite assigns technical security ratings to vendors across a wide range of attack vector domains. However, its large number of data points casts its risk-scoring accuracy into a questionable light.
- Cybersecurity Reporting Workflows: The platform’s strategy report feature allows cybersecurity risk posture insights to be readily shared with stakeholders.
Black Kite’s performance against key Vendor Risk Management metrics
Below is an overview of how Black Kite performs against three primary performance metrics collectively representing the usability and reliability of a VRM tool.
- User-Friendliness: The Black Kite platform is relatively intuitive and quick to implement.
"Some features are delayed longer than what is promised, the platform is very easy to use, but some information can be a bit hard to find. Also, some features of the platform provide great information but do not provide evidence always, so you sometimes need to confirm information manually to ensure that it is accurate."
- 2023 Gartner Review
- Customer Support: Users are reportedly not very pleased with the company’s level of customer support.
Customer service - they have no interest in fixing their product. Duplicate findings. Old findings that rarely get rescanned."
- 2022 Gartner Review
- Risk Scoring Accuracy: Black Kite does not combine external vendor risk monitoring with assessment workflows, forcing users to implement a separate TPRM solution if they want to establish a comprehensive risk assessment program. Without integrated risk discovery pathways mapping from in-built risk assessment workflows, the platform’s ability to consider the complete scope of potential third-party risk factors in its risk scoring methodology is questionable.






