Both proxy servers and VPNs hide your IP address, allowing you to access websites anonymously, but only VPNs direct all network traffic through an encrypted tunnel.
Another key difference is that VPNs address all network data while proxy servers only operate on an application level.
The differences between the two solutions can be summarized as follows:
Both proxy servers and VPNs allow users to access web content securely, but only VPNs offer complete user privacy protection.
Before diving into their technical differences, its important to first solidify your understanding of proxy servers and VPNs.
What is a Proxy Server?
A proxy server is a middleman between a user and web server. When internet activity passes through this remote server, a user's IP address is replaced with the IP provided by the proxy server.

A proxy server can do a lot more than just hide your IP address. It could be configured to act as a firewall and an internet connection filter for blocking malware injection attempts.
Learn more about Proxy Servers.
There are several different types of proxy servers to address popular internet traffic use-cases impacting cybersecurity.
Forward Proxy
A forward proxy service monitors internal network traffic. This proxy is situated at the edge of an internal network, between internal users and the internet.
Forward proxies refer to specified administrative controls to either approve or deny connection requests between users and the internet.
Forward proxies offer very basic IP address security and cannot address complex user access requirements.

Forward proxies can be used for:
- Monitoring internal network activity
- Caching website data to increase web browser speed
- Monitoring employee internet behavior
- Blocking potentially malicious traffic
- Blocking staff access to certain web pages
Reverse Proxy
A reverse proxy is situated further away from the users in comparison to a forward proxy. All outbound traffic is filtered through a reverse proxy which then regulates each application server request in accordance with policy management guidelines.

Reverse proxiess can be used for:
- Securing application connections through TCP three-way handshakes
- Approving or blocking user connection requests
- Connecting users to an origin server
Learn more about reverse proxies.
Transparent Proxy
A transparent proxy server works by clandestinely filtering online activity without notifying users. By automatically routing all traffic through a transparent proxy, users are able to instantly browse the internet anonymously without administrative delays.
But this seamless experience comes with some serious consequences. Transparent proxies are potential attack vectors for SYN-flood-denial-of-service attacks.
It's important to understand that transparent proxies do not conceal a user's identity from targeted web servers. A user's information, including their IP address, is supplied in each connection request header.
Transparent proxies can be used for:
- Filtering out unwanted content as specified by proxy policies
- Monitoring traffic within a private network
- Forcing user authentication when joining a network
Anonymous Proxy
Anonymous proxies have almost the opposite function of transparent proxies. They conceal all identifying information from targeted servers to support anonymous browsing.
Because complete online anonymity is an essential requirement for most cybercriminal activity, governments sometimes set up anonymous proxies to capture the identity of cybercriminals hoping to cloak their online attacks.

Anonymous proxies are commonly used for:
- Blocking identity theft attempts
- Controlling access to sensitive information
- Anonymizing app messages
Other types of proxies include:
- SOCKs proxies (SOCKS4 and SOCKS5)
- Distorting proxies
- Residential Proxies
- Datacenter Proxies
- Shared Proxies
- Public Proxies
- Rotating Proxies
What is a Virtual Private Network VPN?
A VPN encrypts all sent and received data on the internet to allow users to browse the internet in complete privacy.
In addition to completely encrypting all traffic, VPNs also hide IP addresses and allow users to change their location so that geo-restricted content can be accessed. For example, Netflix content that’s only available in certain countries can be unblocked using a VPN.
VPNs are often confused with Tor browsers but these are two different solutions.
How Does a VPN Work?
Without a VPN, network data is transferred with complete transparency between a user, their Internet Service Provider (ISP), and the internet.

When a VPN is implemented, all network data streaming from a user's device is passed through a VPN client before the ISP receives it. This conceals your web query from your router and instantly encrypts traffic to prevent the ISP from reading it.
As the encrypted traffic leaves the ISP, it passes through a VPN server to prevent accessed websites from collecting identifying data from users.
This encryption works in both directions to facilitate secure and anonymous browsing at all times, even when public Wi-FI hotspots are in use.
VPNs secure network traffic at the operating system level, which covers a much wider bandwidth of protection compared to proxy servers. At the operating system level, all traffic is redirected to VPN encryption tunnels.
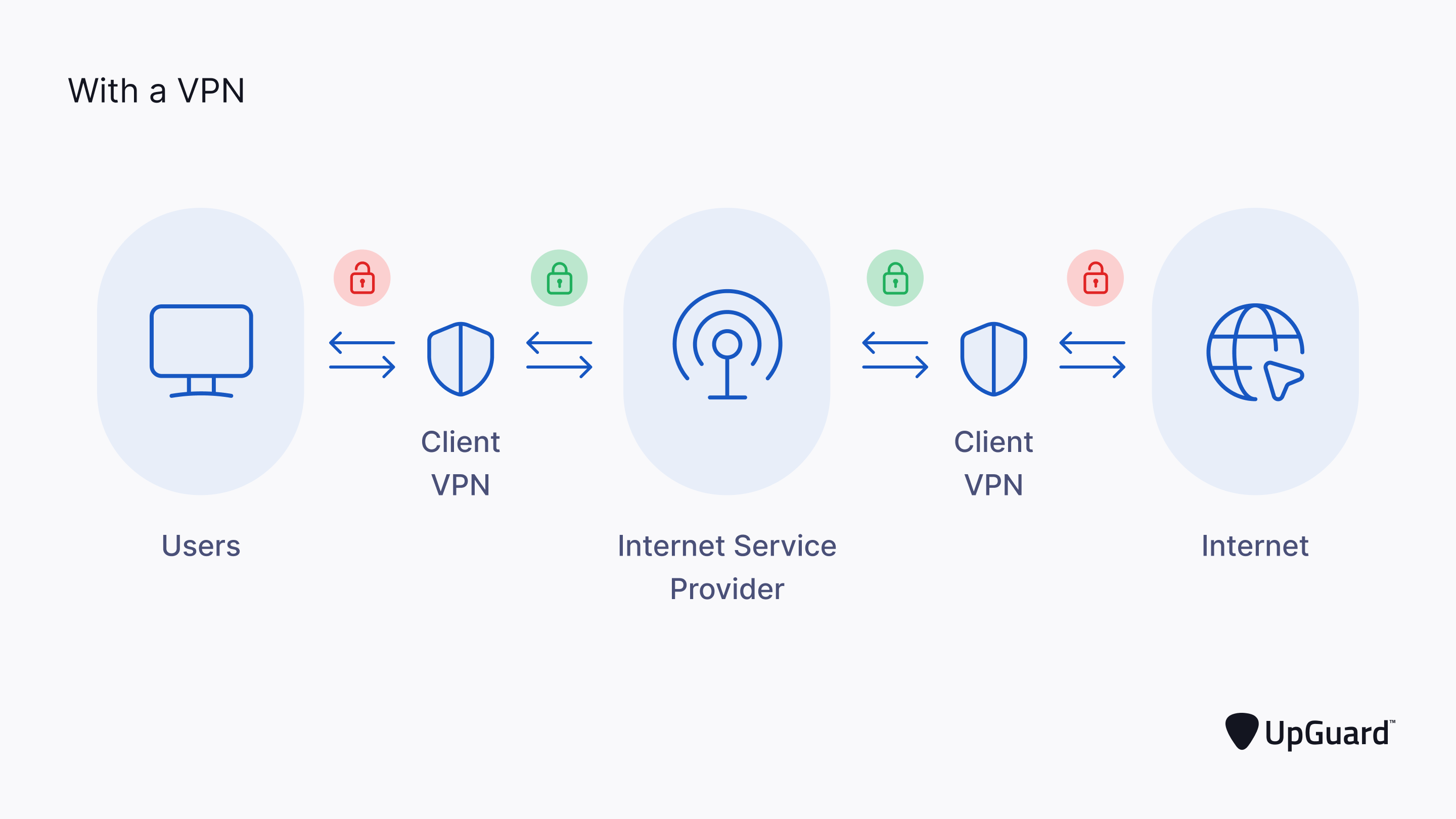
Because VPNs hide a user's IP address and provide end-to-end encryption, it's the ideal solution for mitigating malicious snooping inside private networks.
3 Key Differences Between Proxy Servers and VPNs
When considering a more secure internet browsing experience, both proxy servers and VPNs are usually at the top of the recommendation list.
1. VPNs offer greater user security
Only VPN connections completely encrypt network traffic. Some proxies incorporate SSL certificates when transferring data but this strategy doesn't provide the same level of protection as the end-to-end encryption offered by VPNs.
When SSL certificates are used, web traffic is vulnerable to hacker interception through a type of cyberattack known as SSL stripping.
That being said, because both VPNs and proxy servers hide a user's IP address and therefore the identity of their device, both options could protect users from DDoS attacks and Brute Force attacks.
For the greatest level of sensitive data protection when browsing the internet, it’s best to steer clear of proxy servers (especially free proxy servers) and settle for a VPN service by a trusted VPN provider.
2. VPNs offer greater privacy
VPNs offer significantly higher levels of privacy compared to proxy servers. This is because, unlike proxy servers, VPNs offer end-to-end encryption - the main feature that elevates VPNs across all security use-case scenarios when compared to web proxies.
Because VPNs conceal a user's IP address and browsing activities, the level of privacy that's possible with this security control is capable of even preventing governments from monitoring web users. This is why the Chinese Government is hoping to restrict public access to VPN services.
3. VPNs offer faster browsing speed
Internet connections passing through a VPN are usually significantly faster than those passing through a proxy.
One of the reasons why this is the case is that VPNs don't have web log policy, because they encrypt all connection requests. Proxy servers, on the other hand, do log all traffic.
Users might notice a slight drop in connection speed with a VPN when they play online games at extreme definition settings.
Do You Need to Use a Proxy if You Have a VPN?
No, it's unnecessary to couple a proxy with a VPN because the best VPNs are already hiding a user's IP address. It's a superfluous effort to also direct traffic to a proxy server to further conceal your IP address that will only result in slower browsing speeds.
Should You Use a Free VPN or a Free Proxy Server?
Free security solutions could introduce software vulnerabilities into your IT ecosystem, which will negate the security benefits you're hoping to gain from these solutions. So it's best to avoid free VPNs and proxies.
Free proxies and VPNs also often significantly slow down internet connection speeds.
Final Thoughts
For the greatest level of sensitive data and cyberattack protection, a VPN should be preferenced over a proxy server.
The end-to-end encryption feature of VPNs prevents cybercriminals from intercepting and stealing your sensitive data in transit. By concealing your IP address, VPNs also obfuscate location-specific cyberattacks, such as DDoS attacks and Brute Force attacks.






