Efficient cyber threat detection is the cornerstone of an effective cybersecurity program. This post ranks the top eight cyber threat detection tools dominating the cybersecurity solution market in 2025.

A Complete Guide to Data Breaches
Download this eBook to learn how to avoid a costly data breach with a comprehensive prevention strategy.
What is a cyber threat detection tool?
A cyber threat detection tool identifies potential security threats targeting an organization's network and assets before they escalate into a security incident. These tools provide critical insights into vulnerabilities and malicious activities, enabling security teams to have advanced awareness of potential security incidents.
While primarily focused on threat detection, the most effective solutions also support every phase of the cyber threat detection and response lifecycle:
- Detection: Identifying anomalies, suspicious activities, or indicators of compromise within a secure network
- Investigation: Determining the nature, scope, and potential impact of detected threats to prioritize response measures effectively
- Containment: Isolating affected systems to prevent further compromise
- Eradication: Eliminating all traces of the cyber threat from impacted systems
- Recovery: Restoring normal operations with minimal disruption to business activities
- Reporting: Documenting the incident, including the findings, response steps, and lessons learned, for future reference and compliance
- Prevention: Utilizing the insights gained from threat detection to strengthen defenses and reduce the likelihood of similar threats recurring
5 key features of the best cyber threat detection tools
To effectively safeguard an organization from cyber threats, a top-tier cyber threat detection platform should include the following essential features:
- Detection of active and dormant cyber threats: For the greatest cyber threat spectrum coverage, the tools should address both active threats, such as phishing, ransomware, and supply chain attacks, and dormant vulnerabilities, like unpatched systems zero-day exploits.
- Actionable threat intelligence insights: All collected cyber threat insights should be delivered to support streamlined and efficient remediation responses. This reporting includes providing remediation recommendations based on identified cyber threats.
- Third-party risk detection: Given the significant role of third-party vendors in cybersecurity incidents, an ideal solution should extend its cyber threat detection capabilities to the third-party attack surface.
- Scalability: The tool should effortlessly support an expanding cyber threat detection program, ideally through automation features.
- Insider Threat Mitigation: To be a worthwhile investment, a cyber threat detection tool should address the most dangerous category of cyber threats, insider threats.

A Complete Guide to Data Breaches
Download this eBook to learn how to avoid a costly data breach with a comprehensive prevention strategy.
List of the Best Cyber Threat Detection Tools in 2025
The tools ranked in this list have been evaluated based on how effectively they align with the five key features of an ideal cyber threat detection solution.
1. UpGuard
UpGuard is a comprehensive platform designed to manage attack surfaces and third-party risks. UpGuard provides a unified solution for addressing the entire lifecycle of cyber threats by integrating external attack surface intelligence with end-to-end risk management capabilities.
Below, we evaluate UpGuard’s performance against the five essential features of an ideal cyber threat detection tool.
Detecting active and dormant cyber threats
The UpGuard platform can identify and mitigate active and dormant cyber threats, ensuring comprehensive visibility into potential sources of data breaches and supply chain attacks.
Key features include:
- Threat intelligence feed: The UpGuard platform includes a continuously updated news feed of all security incidents impacting your organization through your vendor ecosystem. During the CrowdStrike incident, UpGuard’s feed enabled users to quickly identify and address the impacted third-party vendors in their ecosystem.
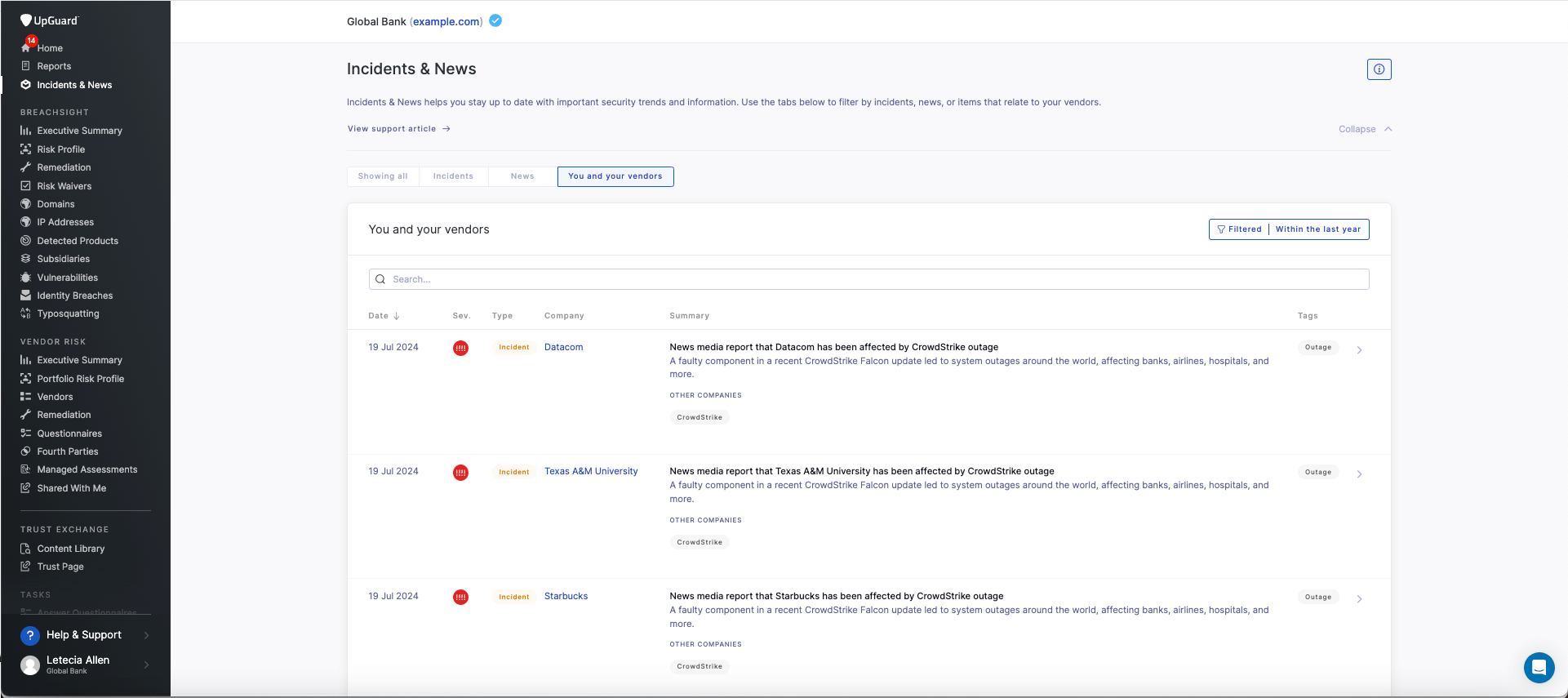
UpGuard's incident and news feed help users respond efficiently to the CrowdStrike security incident by highlighting all impacted vendors.
- Dark web disclosures: UpGuard's dark web monitoring features continuously scan criminal forums and ransomware blogs for exposed credentials and sensitive data leaks that could facilitate security incidents.

2. Actionable cyber threat intelligence insights
UpGuard delivers actionable insights by providing detailed vendor risk profiles and highlighting their impact on your organization. The platform detects these risks through automated IPv4 web space scans completed in just 24 hours, one of the industry's fastest third-park risk scan refresh rates.
Key features include:
- Risk categorization and prioritization: All identified risks are ranked by severity across ten categories, including IP and domain reputation, website security, encryption, vulnerability management, network integrity, email security, data leakage, DNS issues, attack surface vulnerabilities, and brand reputation, for the most comprehensive coverage of all potential data breach attack vectors.

- Detailed risk analysis: The platform’s risk details section provides a breakdown of each vulnerability, including the date the risk emerged, the category it falls under, the number of affected assets, and a description of the underlying issue.

- Remediation Guidance: UpGuard offers detailed remediation recommendations for every listed risk, empowering security teams to take immediate and effective action.

- Subsidiary risk integration: Organizations with subsidiaries can include them in the risk profile view, enabling a unified perspective of shared vulnerabilities. For example, shared issues like the lack of SSL availability across subsidiaries are easily identifiable, facilitating coordinated mitigation efforts.

3. Detection of third-party security risks
UpGuard's platform includes an integrated third-party risk management workflow for addressing the complete lifecycle of vendor-related cyber threats. Key features include:
- Continuous third-party risk monitoring: Real-time insights into the security postures of all monitored vendors, enabling organizations to proactively manage evolving third-party risks before they develop into costly data breaches.
- End-to-end risk assessment workflows: This feature supports the entire lifecycle of third-party cyber threats, from initial detection and assessment to ongoing management and monitoring. T
- Incidents and news feed: This feature helps users keep track of emerging security incidents, such as significant cybersecurity events that may involve their third-party vendors.
Watch this video for an overview of UpGuard's third-party risk assessment workflow:
By leveraging these capabilities, UpGuard empowers organizations to effectively manage and mitigate third-party cyber threat management, strengthening their overall cybersecurity posture.
4. Scalability
UpGuard leverages AI technology to address manual, repetitive tasks that hinder the efficiency of a r third-party cyber threat management program.
Some of UpGuard's automation features supporting cyber threat detection program scalability include:
- AI-Powered questionnaires: UpGuard’s Questionnaire AI continuously learns from your existing library of questionnaires and security documentation to generate fast and accurate responses, reducing the time required to complete questionnaires associated with cyber threat investigation efforts.
- Automatic reporting: Instantly generate stakeholder reports across various formats with a single click.
- Simplified remediation processes: In-built workflows for triage, vendor communications, and risk management make remediation faster and more organized.
Watch this video for an overview of the automation features available in UpGuard Trust Exchange.
Sign up to Trust Exchange for free >
5. Insider threat mitigation
UpGuard takes a unique approach to mitigating insider threats through employee risk scores calculated through insights gathered from three primary human cyber risk factors:
- Identify breaches: Employee credentials that have been compromised in data breaches or other security incidents
- Shadow IT detection: Instances of an employee's unauthorized use of applications and endpoints within the organization’s network
- Third-party service data sharing: Insecure data sharing practices with third-party apps and services breaching cybersecurity policies
Watch this video to learn more about UpGuard's human cyber risk management tool:
2. Recorded Future
Recorded Future is a comprehensive threat intelligence platform that identifies and mitigates risks across various domains, including cyber, supply chain, physical security, and fraud.
Below, we evaluate Recorded Future’s performance against the five essential features of an ideal cyber threat detection tool.
See how Recorded Future compares with UpGuard >
Detection of active and dormant cyber threats
Recorded Future’s Intelligence Cloud gathers insights from a database of global cyber threats, providing real-time, comprehensive, and actionable risk management intelligence. This system offers organizations a holistic view of their evolving attack surface, helping them understand which threats they must prioritize in their mitigation efforts.

For active threats like ransomware, the platform employs a three-layer defense model:
- Threat Intelligence: Delivers real-time insights into emerging ransomware tactics and operations.
- Identity Intelligence: Identifies exposed credentials, helping to mitigate unauthorized access risks.
- Attack Surface Intelligence: Maps vulnerabilities across digital ecosystems to prevent exploitation by ransomware groups.
The platform also monitors for dormant risks that could become a threat in the future, such as brand impersonation attempts, credential leaks, and data exposure. Recorded Future's criminal forum scanning feature also detects compromised credentials to support its active threat mitigation efforts, allowing security teams to shut down compromised accounts before they facilitate ransomware attacks and data breaches.
2. Actionable Cyber Threat Intelligence Insights
Recorded Future’s Intelligence Graph streamlines the collection and analysis of threat intelligence insights from multiple sources. These insights discover relationships across adversaries and IT infrastructures to support early mitigation of cyber threats.
Recorded Future's Collective Insights consolidates internal and external threat data to improve remediation strategies while supporting proactive responses.

3. Detection of third-party risks
Recorded Future offers tools to identify, monitor, and respond to emerging third-party risks, such as:
- Dark web monitoring: The platform scans for evidence of compromised vendors through dark web scans
- Reporting: The platform streamlines reporting of an organization's evolving third-party risk exposure with in-built reporting workflows.
- Fourth-party identification: The tool expands its risk identification scope to the fourth-party landscape, reducing an organization's overall risk of suffering a data breach.
4. Scalability
Recorded Future offers automation features to enhance scalability significantly, allowing organizations to manage a growing volume of security threats more efficiently. These features include alert prioritization, cyber threat contextualization, and workflow automation.
5. Insider threat mitigation
Recorded Future doesn't offer a tool explicitly focused on managing human cyber risks. However, by offering integration capabilities with SIEM and SOAR tools, the platform provides a means of integrating data from other security tools that could broaden the context of potential insider threat activities. Users can also combine insights from SIEM integrations with Recorded Future’s automated threat intelligence and real-time analytics to enhance the detection of internal risks.
3. Cyble vision
Cyble Vision is an AI-driven platform designed to deliver comprehensive threat intelligence by integrating insights from the dark, deep, and surface web. By combining external threat intelligence with real-time monitoring capabilities, Cyble Vision offers a unified solution for identifying and addressing cyber threats.
Below, we evaluate Cyble Vision’s performance against the five essential features of an ideal cyber threat detection tool.
1. Detection of active and dormant cyber threats
By leveraging AI-powered technologies, such as machine learning and natural language processing, Cyble Vision monitors vast datasets across the dark, deep, and surface web. This effort includes scanning TOR, I2P, Paste Sites, and other covert communication channels to identify compromised credentials, leaked sensitive data, and emerging attack vectors.

2. Actionable Cyber Threat Intelligence Insights
Cyble Vision leverages advanced AI capabilities to gather, analyze, and contextualize data from diverse sources, including the deep and dark web, social media, and external threat feeds. The diversity of threat insights provides security teams with a rich cyber threat context for effective risk management.
Cyber Vision's advanced threat analysis technology represents its threat insights through visual representations such as charts and heatmaps, making it easier for security teams to prioritize and act on high-impact cyber risks.
3. Detection of third-party risks
Through advanced analytics and machine learning, Cyble Vision evaluates risks associated with third-party activities, including compromised credentials, leaked sensitive information, and malicious exploitation. These risks are detected from a range of third-party attack vector sources, including the dark web, deep web, and external threat feeds, which makes the tools capable of detecting and preventing cyber chain attack risks.
4. Scalability
Cyble Vision's AI-driven architecture efficiently handles vast amounts of data, including over 350 billion dark web records and 50 billion threat indicators, making it optimal for scaling cyber threat management programs. This scalability makes the tools ideal for diverse architectures spanning multiple geographies.
5. Insider threat mitigation
Cyble Vision integrates with SIEM and SOAR platforms to provide external threat intelligence that could highlight anomalies potentially linked to insider threats. By contextualizing these insights with other internal sources of cyber threat insights, Cyble Vision could support the proactive detection of insider threats.
4. CloudSEK XVigil
CloudSEK XVigil is a comprehensive platform leveraging Cyber Threat Intelligence and Attack Surface Monitoring to proactively predict and prevent threats targeting an organization’s employees and customers. By addressing risks such as phishing attacks, data leaks, dark web exposure, brand misuse, and infrastructure vulnerabilities, XVigil delivers robust protection against evolving cyber threats.
Below, CloudSEK XVigil's performance is evaluated against the five essential features of an ideal cyber threat detection tool.
1. Detection of active and dormant cyber threats
CloudSEK XVigil detects active and dormant threats by leveraging continuous monitoring across the surface, deep, and dark web. The platform scans thousands of sources, including dark sites, marketplaces, forums, and communication channels like IRC and I2P, to identify exposed assets and malicious activities.
With its proprietary AI-based algorithms, CloudSEK XVigil correlates discovered threats with an organization's digital assets, enabling timely identification of vulnerabilities such as credential leaks, data breaches, and phishing sites.

2. Actionable Cyber Threat Intelligence Insights
CloudSEK XVigil compares threat insights from the surface, deep, and dark web with an organization's assets to detect various security risks. The platform leverages AI technology to analyze large datasets in real time, identifying threats such as credential leaks, fake domains, phishing attempts, and rogue applications. The platform combines detailed threat analysis reporting with high-priority alerts so that security teams can effectively leverage these insights to respond promptly to discovered cyber threats.
3. Detection of Third-Party Risks
CloudSEK XVigil’s third-party risk detection efforts primarily focus on its takedown services that aim to protect an organization’s brand reputation. The platform identifies threats such as phishing sites, fake domains, infringing social media accounts, and rogue applications on third-party app stores and shuts them down with a dedicated takedown team.
4. Scalability
CloudSEK XVigil's modular architecture optimizes the platform for scaling. Users can choose to onboard different threat detection modules when and if they are required as a cybersecurity program grows—such as Deep and Dark Web Monitoring, Brand Threat Monitoring, and Data Leak Monitoring.
The platform also supports unlimited users and IT assets, making it ideal for organizations with an extensive digital footprint.
5. Insider threat mitigation
CloudSEK XVigil's integrations with SIEM and SOAR platforms allow users to compare external threat intelligence with internal security data to discover potential insider threat activities. This effort is supported by APIs, Syslogs, STIX, and TAXII feeds, which collectively integrate with broader security infrastructures to broaden the context of potential insider threat activities.
5. Trustwave
Trustwave specializes in delivering Managed Detection and Response (MDR), Managed Security Services (MSS), database security, and email security solutions to organizations worldwide. With a focus on proactive threat management and robust security operations, Trustwave empowers businesses to offload most of their threat identification efforts to reduce internal security resource strain.
Below, Trustwave's performance is evaluated against the five essential features of an ideal cyber threat detection tool.
1. Detection of active and dormant cyber threats
Trustwave’s Managed Detection and Response (MDR) is a comprehensive service that leverages Trustwave’s expertise and cutting-edge technologies to eliminate evolving cyber threats. The MDR services offer 24/7 monitoring and proactive threat hunting across an organization's IT infrastructure. Supported by Trustwave SpiderLabs, the service focuses on cyber threat identification and mitigation, allowing organizations more time to focus on proactive cybersecurity initiatives.

2. Actionable cyber threat intelligence insights
The Trustwave Fusion platform contextualizes multiple streams of cyber threat insights, including existing security tools and infrastructure. When a cyber threat is identified, Trustwave’s MDR services investigate, triage, and, if required, take predefined response actions. Leveraging Trustwave's MDR service eliminates false threat alerts and supports security team productivity by minimizing internal resource fatigue.
3. Detection of third-party risks
Trustwave’s Managed Detection and Response (MDR) service supports the detection of third-party risks by providing continuous monitoring and event correlation across an organization’s extended environment. This service leverages the insights produced from advanced telemetry to identify potential vulnerabilities within third-party systems.
4. Scalability
Trustwave supports scalability by focusing on rapid time-to-value, resulting in new clients being onboarded in as little as 10 days. This framework comprises five strategic phases - mobilization, planning, deployment, operational readiness, and steady-state operations.
5. Insider threat mitigation
Trustwave highlights potential insider threat activities through the Trustwave Fusion platform. Fusion integrates cyber threat data feeds from multiple security tools to provide real-time insights into suspicious activities and policy violations potentially associated with insider threats. The expertise of the Trustwave SpiderLabs team further enhances this capability by highlighting subtle threat patterns and offering actionable guidance for addressing them.
6. CrowdStrike Falcon
CrowdStrike Falcon is a comprehensive endpoint protection platform that monitors internet connections to identify and block malicious activities. The platform is very effective at proactively detecting and stopping advanced cyber threats by mapping IOCs to the MITRE ATT&CK framework.
Below, CrowdStrike Falcon's performance is evaluated against the five essential features of an ideal cyber threat detection tool.
1. Detection of active and dormant cyber threats
CrowdStrike Falcon leverages AI-powered indicators of attack (IOAs) and advanced telemetry analysis to highlight developing cyber threats. The platform also uses machine learning methods to continuously monitor endpoints, identities, and cloud workloads to detect fileless attacks and suspicious activities potentially linked to developing active threats.
Falcon encourages a proactive cyber threat defense strategy through its Falcon OverWatch feature, which aims to identify and block sophisticated cyber threats before they escalate into security incidents.

2. Actionable cyber threat intelligence insights
The CrowdStrike Falcon platform integrates cyber threat insights from multiple attack vectors to provide a rich overview of an organization's cyber risk posture. These insights are monitored with real-time indicators of attack mapping to the MITRE ATT&CK framework to provide security teams with sufficient context to intercept threats as quickly as possible. Falcon also leverages AI-driven intelligence to predict adversary behavior and support a proactive approach to cyber risk management.
3. Detection of third-party tasks
CrowdStrike extends its threat detection capabilities into the external attack surface with features like Falcon OverWatch and Next-Gen SIEM. Together, these capabilities allow monitoring of potential third-party cyber risks associated with vulnerable supply chain profiles.

4. Scalability
The platform's cloud-native architecture and index-free data management process optimize it for seamless scaling. Falcon also offers automated deployment and integration capabilities, making it an ideal solution for scaling enterprises.
5. Insider threat mitigation
CrowdStrike Falcon mitigates insider threats through its Asset Graph feature. Asset Graph offers complete visibility into all managed and unmanaged IT assets, mapping how devices, users, applications, accounts, and systems interact in an organization's attack surface. By integrating this data into a unified graph, Falcon makes it easier to spot potential insider threat activities, such as unauthorized access attempts. Such a dynamic visibility field allows security teams to proactively respond to insider threat risks before they develop into security incidents.

7. Rapid7 InsightIDR
Rapid7 InsightIDR is a Security Information and Event Management (SIEM) platform designed to collect and analyze cyber threat insights across an organization's IT environment.
Below, Rapid7 InsightIDR's performance is evaluated against the five essential features of an ideal cyber threat detection tool.
1. Detection of active and dormant cyber threats
Rapid7 InsightIDR combines machine learning, User and Entity Behavior Analytics (UEBA), and curated threat intelligence to detect both active and dormant threats. The platform continuously tracks network, user, and endpoint activity, integrating diverse telemetry data to detect anomalies and behavioral patterns associated with advanced cyberattacks.

2. Actionable cyber threat intelligence insights
InsightIDR integrates internal and external cyber threat insights, such as attack surface maps and global threat insights, into a single unified dashboard. The tool's dashboard is designed to encourage rapid threat response, with alerts highlighting critical risks to prioritize and embedded reporting tools supporting enhanced decision-making across complex environments.
3. Detection of third-party risks
InsightIDR offers insights into third-party risks through its integration capabilities. The platform's access to external threat intelligence also allows it to highlight risks associated with vendor activities and potential supply chain exposures.
4. Scalability
With its cloud-native architecture capable of ingesting large datasets, InsightIDR has been developed to be highly scalable. The platform has a data retention policy of 13 months to mitigate performance lag during scaling. For new users, the tool is very quick to onboard, and with flexible integration options, InsightIDR supports dynamic and growing environments
5. Insider Threat Mitigation
Rapid7 InsightIDR detects insider threats using User Behavior Analytics (UBA) to continuously monitor for potentially malicious behavior outside of baseline normal activities. When suspicious activity is detected, these events are tied to specific users to be monitored more closely. The tool also sets up intruder traps to detect common data breach attack vectors and stop intruders earlier in the attack chain.
8. WildFire (by Palo Alto)
WildFire is a cloud-based malware protection engine utilizing machine learning and crowdsourced intelligence to protect against a wide range of malware variants. The tool offers organizations a proactive defense against evolving cyberattacks.
Below, WildFire's performance is evaluated against the five essential features of an ideal cyber threat detection tool.
1. Detection of active and dormant cyber threats
WildFire by Palo Alto Networks leverages machine learning to intercept active threats like ransomware and malware. This detection capability occurs at the firewall level to detect active threats in the early stages of the attack chain. The platform integrates dynamic and static network analysis to highlight various malicious behavior characteristics, providing comprehensive coverage for web, email, and file-sharing protocols.

2. Actionable cyber threat intelligence insights
By combining dynamic unpacking techniques with its custom-built hypervisor, Wildfire can detect cyber threat insights from an even greater range of files while preventing sandbox evasion - a method cyber criminals use to avoid detection in a cyber threat analysis environment.
3. Detection of third-party risks
Through its Open API, Wildfire supports integrations with third-party security tools, like SIEM systems, enabling access to third-party risk insights that could be useful for cyber threat forensics. However, the Wildfire platform doesn't include an in-built third-party risk management workflow to address all vendor cyber threats.
4. Scalability
Wildfire's cloud-based architecture supports massive-scale deployments for cloud environments of all sizes. The solution's subscription-based model allows users to seamlessly scale their use of the platform without compromising performance.
5. Insider threat mitigation
Wildfire addresses insider threats with its Precision AI feature. This tool uses deep learning models trained on diverse cyber threat data sets to detect subtle anomalies characteristic of insider threats. Precision AI continuously improves based on new attack method data to maintain its effective detection capabilities in an evolving threat landscape




