Compliance management is the process of ensuring all workflow, internal policies and IT initiatives align with specific industry cybersecurity regulations. This effort is ongoing since the digital attack surface is always expanding.
Why is Compliance Management Important?
Compliance management is important because the penalties for non-compliance with cybersecurity regulations are extremely severe. Regulatory compliance policies are especially stringent for financial institutions and healthcare entities because of the highly sensitive customer information they store.
To appreciate the severity of potential fines for non-compliance in these industries, consider the following example penalities for current cybersecurity regulations.
- The penalty for non-compliance with the Health Insurance Portability and Accountability Act of 1996 (HIPAA) alone can range from $100 to $50,000 per individual violation.
- The penalty for non-compliance with the Payment Card Industry Data Security Standards (PCI DSS) ranges from $5,000 to $10,000 per month until compliance is achieved.
If a compliance audit discovers multiple compliance responsibilities across business units (which is usually the case), the potential penalties multiply. The GDPR - a popular regulatory requirement that usually accompanies other compliance requirements - has a maximum violation penalty of €20 million (about 23 million USD) or 4% of annual turnover (whichever is larger).
But compounding violation penalties is not the only reason stakeholders should pursue effective compliance management. The primary benefit of corporate compliance is the resulting improvements in security postures across all business functions.
Cybersecurity compliance activities ensure businesses meet the minimum benchmarks for cyber resilience. The Essential Eight is an example of a risk management compliance program that results in such a positive development.
When its eight security controls are implemented, the Essential Eight helps senior management align business processes with world-class cybersecurity disclosures, despite initial cybersecurity maturity levels.
An Overview of an Effective Compliance Management System
Effective compliance risk management is a bilateral approach. Compliance teams must simultaneously monitor for security risks breaching legal requirements and deploy corrective action to remediate these compliance issues - all while keeping stakeholders and the board of directors continuously informed of compliance efforts.
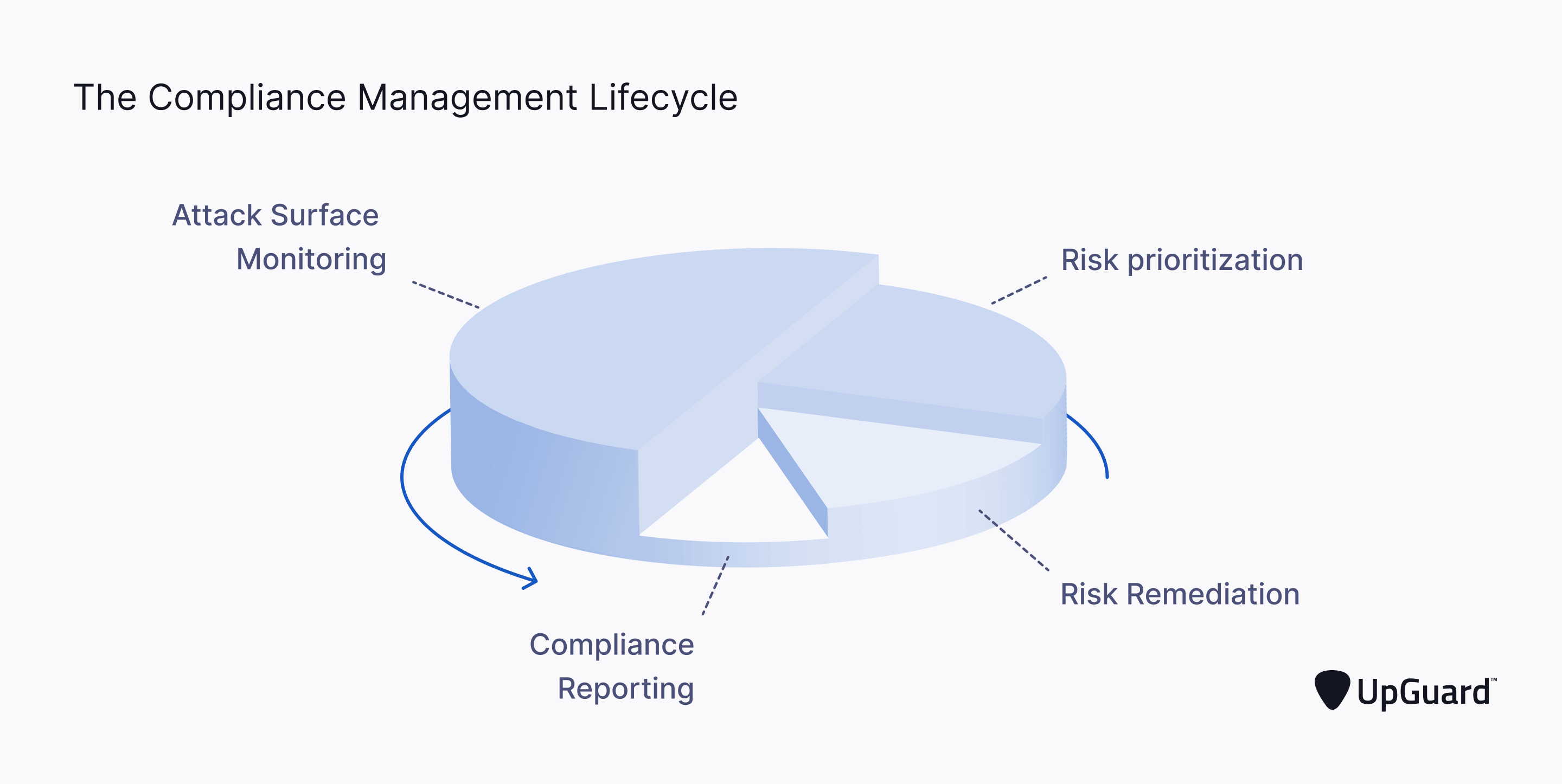
Such an effective compliance lifecycle is most easily achieved by distributing these responsibilities across four primary pillars:
- Monitor attack surface - Identify security vulnerabilities and system flaws breaching compliance thresholds across all applicable regulations.
- Prioritize risks - Organize all identified security vulnerabilities by degree of potential impact on sensitive data and level of potential non-compliance penalty.
- Remediate risks - Quickly address security risks starting with the most critical security tier as organized in the preceding step.
- Report compliance efforts - Document compliance efforts to keep senior management and auditors informed of your efforts.
Third-party security risks impacting compliance add another dimension of complication to compliance management efforts. These factors are best addressed in a separate cyber program known as Vendor Risk Management. Segregating internal and external compliance factors will make managing your overall compliance strategy easier.
Most Common Cyber Compliance Management Challenges
Despite its intuitive design, many organizations still struggle to commit to a compliance management framework. This disruption is caused by three major challenges. Advanced knowledge of these challenges could help security teams avoid their costly consequences.
Challenge #1 - The Attack Surface is Rapidly Expanding
Mass adoption of cloud technology is rapidly expanding the attack surface, giving cybercriminals many more attack vector options to choose from. Without the right supporting solutions, managing risk assessments that measure compliance violations across the third-party provider network is a logistical nightmare.
Challenge #2 - Cybersecurity Solutions are not Scalable
As organizations expand their infrastructures into cloud environments and then continue to scale, conventional cybersecurity strategies often lag behind.
This lag prevents the rapid detection of security vulnerabilities arising from the expanding attack surface, resulting in gaping compliance deficits.
Poor scalability is usually caused by the dense infrastructures of common cybersecurity solutions and the monumental costs required to expand them.

Challenge #3 - System Complexity
Modern corporate environments, with their multi-tiered and geographically dispersed infrastructures, are very complicated - and that's without the added complexities of cybersecurity solutions.
Coordinating compliance management policies and timely compliance reporting across such a diverse and expansive environment is not easy.
Best Practices to Streamline Compliance Management in 2023
Common compliance management challenges can be readily overcome by following best practices and implementing solutions supporting these efforts.
The following four best practices will help you efficiently manage all of your regulatory compliance obligations and overcome the common pitfalls disrupting this ongoing effort.
1. Continuously Scan the Entire Attack Surface
Continuously scanning the entire attack surface will help you rapidly identify and address security issues impacting compliance before they're exploited by cybercriminals.
UpGuard continuously scans both the internal and third-party attack surface to keep security teams aware of all potential security flaws disrupting regulatory compliance. This convenient single-pane-of-glass view across the entirety of the attack surface allows internal audits to occur more frequently and at speed, further reducing the potential of non-compliance penalties.

2. Assign a Security Criticality Rating for Each Vendor
Third-party vendors introduce new security risks into an ecosystem that could violate the cybersecurity standards of regulations. Some vendors pose a greater risk than others and must be addressed to minimize impact.
Categorizing vendors by degree of potential security risks helps security teams keep critical vendors always at the top of their priority list.
Vendor Tiering is a powerful feature available on the UpGuard platform that allows security teams to classify vendors based on their assigned degree of security risk. The tiering process is manual, allowing you to assign each vendor to a criticality category based on your unique security expectations and vendor assessment responses.

3. Adopt Managed Services for Third-Party Risk
To overcome the scaling challenges of conventional cybersecurity solutions, managed services should be adopted for third-party risk programs. This will address the most complicated component of cybersecurity scaling - keeping up with the expanding vendor network.
A single business can quickly become overwhelmed with security vulnerabilities if this expansion occurs across multiple third-party vendors.
UpGuard offers fully managed third-party risk and data leak detection services by a team of expert analysts and an AI-assisted platform. These analysts can be readily augmented with internal security teams, allowing organizations to rapidly scale their third-party cybersecurity efforts in line with their expanding vendor network.
4. Monitor Compliance Gaps Across Popular Cybersecurity Regulations
The unique security risks introduced by newly onboarded vendors have a direct impact on an organization's ability to meet its regulatory standards. Each third-party vendor is also likely bound to its own unique set of regulations that could prevent security risks from permeating into your IT network.
Vendor Risk by UpGuard maps the security efforts of each third-party vendor against popular cybersecurity frameworks to help you identify and address the specific deficiencies preventing complete compliance.






