What is Vendor Risk Monitoring in Cybersecurity?
Vendor risk monitoring is the process of continuously identifying, assessing, and managing security risks associated with third-party vendors. This effort is crucial to a successful Vendor Risk Management program as it ensures an organization’s third-party risk exposures remain within acceptable levels throughout each vendor's lifecycle.
In a Third-Party Risk Management (TPRM) program, vendor monitoring primarily focuses on two risk categories:
- Cybersecurity risks: Cyber risks and vulnerabilities in the supply chain increase your risk of being impacted by a data breach.
- Regulatory compliance risks: Misalignments with regulatory standards due to a vendor’s information security practices.
Depending on the risk mitigation objectives set by your stakeholders, a vendor risk monitoring solution could also track the following areas of risk exposure:
- Financial risks: Potential risks, such as security exposures, reputational risks, or data leaks, that could have a detrimental financial impact on the business.
- Business continuity risk: Operational risks and service disruptions caused by third-party vendors, such as the ubiquitous CrowdStrike incident.
What is continuous vendor security monitoring?
Continuous vendor security monitoring is the ongoing, real-time assessment of vendor security postures to detect and mitigate emerging risks. Unlike one-time or periodic vendor risk assessments, continuous risk monitoring provides dynamic insights into a vendor’s cybersecurity performance, keeping you up-to-date on any new potential risks.
Benefits of continuous vendor security monitoring
Continuous vendor security monitoring includes the same benefits as one-time security assessments. Still, ongoing monitoring allows organizations to track a vendor’s security posture over time—identifying problem areas as they appear.
Benefits of continuous security monitoring include:
- Reducing the risk of third-party breaches: Identify and mitigate vulnerabilities before they become breaches
- Minimizing regulatory non-compliance fines: Ensures organizations remain compliant with evolving cybersecurity laws
- Strengthening incident response: Streamlines detection, which leads to quicker addressing of third-party threats and prevents disruptions
- Building vendor accountability: Encourages vendors to maintain stronger security postures and vendor performance over time
What is the difference between vendor risk monitoring and vendor risk assessments?
Unlike traditional point-in-time assessments, which occur through vendor risk assessments, vendor risk monitoring involves ongoing tracking of emerging vendor risks. This process is also called “continuous monitoring” in Vendor Risk Management (VRM). When used in conjunction with point-in-time methods, continuous monitoring processes provide real-time awareness of emerging risks, even between risk assessment schedules.

To help security teams efficiently track continuous monitoring data for multiple vendor relationships, risk monitoring insights are typically quantified as a security rating to produce a risk score representing each vendor’s security posture. Security ratings are calculated by considering multiple risk categories potentially impacting vendor performance across cybersecurity and reputational impact metrics.
Depending on how important financial and continuity risk monitoring are to your risk management objectives, it might be most cost-efficient to implement a security rating tool for monitoring vendors against cyber attacks and reputational risks caused by poor security control practices.

Why is vendor risk monitoring important for Vendor Risk Management?
VRM programs are now dependent on a vendor risk monitoring component for three primary reasons:
1. The vendor ecosystem is dynamic
With digital solutions increasing integrations between service providers and AI technology being adopted en masse, a VRM program now requires a vendor monitoring component to keep up with emerging third-party vendor risks. A highly vendor-centric ecosystem also presents TPRM teams with the problem of keeping track of their rapidly expanding attack surface. To address this, the scope of vendor risk monitoring has been expanding to include the detection of unmaintained technologies.
Watch this video for an overview of how risk monitoring could be used to detect technology products in your attack surface.
2. Regulatory compliance is more contingent on effective third-party risk management
Third-party vendors continue to be one of the primary factors contributing to an organization’s data breach risks, and as a result, regulatory bodies are increasingly mandating continuous oversight of third-party vendors. These stringent vendor risk management process standards are especially being introduced in industries handling highly sensitive information and customer data, such as healthcare, finance, and critical infrastructure.
The Federal Reserve System, Federal Deposit Insurance Corporation, and the Department of the Treasury are just a few examples of agencies that have recently bolstered their third-party risk management standards.
Regulations often require organizations to maintain ongoing visibility into each vendor’s risk levels and have protocols in place for rapidly responding to discovered risks.
A vendor risk monitoring process that satisfies most regulatory requirements of enhanced third-party risk management typically involves security questionnaires mapping to popular standards, such as GDPR, HIPAA, NIST CSF, and PCI DSS.
The following video explains how a vendor risk monitoring solution can be leveraged to track and manage compliance in a highly regulated sector like finance.
Learn how UpGuard is protecting financial services >
To streamline the remediation process of discovered regulatory compliance risks, an ideal vendor risk monitoring tool must be capable of separating high-risk vendors through a vendor tiering model so that critical compliance risks can be readily prioritized.

3. Proactive risk management
One of the most significant benefits of vendor risk monitoring is its support of real-time risk detection and, as a result, rapid remediation responses. According to IBM, the cost of a data breach is directly proportional to the time taken to respond to an incident.
An efficient vendor risk monitoring solution could provide advanced awareness of third-party risks before they develop into security incidents, which could also reduce the significant financial, operational, and reputational risks associated with data breach events.
What is involved in the vendor monitoring process?
Vendor risk monitoring is involved across all the major stages of the Vendor Risk Management lifecycle.
1. Onboarding
During the onboarding stage of VRM, vendor risk monitoring is leveraged to streamline due diligence workflows by expediting the sourcing of certifications, completed questionnaires, and other security documentation for new vendors. Once completed, the vendor monitoring component of due diligence identifies high-risk vendor partnerships requiring more focused monitoring throughout their relationships.
A vendor monitoring process could also identify instances of risk appetites, with superficial risk scores identifying potential vendors who should be disqualified from onboarding considerations.
2. Ongoing risk assessments
Once onboarded, the types of risks that need to be addressed in a third-party risk treatment plan must be actively managed through a combination of point-in-time assessments and continuous monitoring, ideally within a single Vendor Risk Management solution. This critical phase of vendor risk monitoring ensures an organization's third-party risk exposure remains within tolerance levels.
Fourth-party risks can be accounted for through comprehensive risk monitoring coverage. This capability proved to be a competitive point of differentiation for VRM platforms during the global Crowdstrike incident.
This video demonstrates how extending risk monitoring to the fourth-party landscape benefits VRM efforts during global disruptions like the CrowdStrike event.
3. Automated risk scanning
Automated risk scanning continuously evaluates a vendor’s external security posture by detecting vulnerabilities, misconfigurations, exposed assets, and compliance issues. This type of risk scanning automation operates similarly to attack surface management tools, scanning for cybersecurity risks like security gaps that attacks might exploit.
Automated risk scanning includes:
- Identifying vulnerabilities such as open ports, weak encryption, and expired SSL certificates
- Monitoring changes in vendor environments that could introduce security risks
- Ensuring vendors follow best practices by assessing their security hygiene over time
4. Live intelligence feeds
Live intelligence feeds. collect dynamic cybersecurity threat data from various sources, including government agencies, cybersecurity firms, and global information security networks. These feeds provide up-to-date information on new vulnerabilities, active exploits, and evolving threats. Organizations can then use this information to cross-check their vendor ecosystem for new vulnerabilities or exploits.
Live intelligence feeds include:
- Informing security teams of new attack techniques targeting third-party service providers
- Providing early notifications about vendor-related threats before they escalate into data breaches
- Allowing companies to adjust security controls based on real-world threats—enabling a proactive approach to risk mitigation
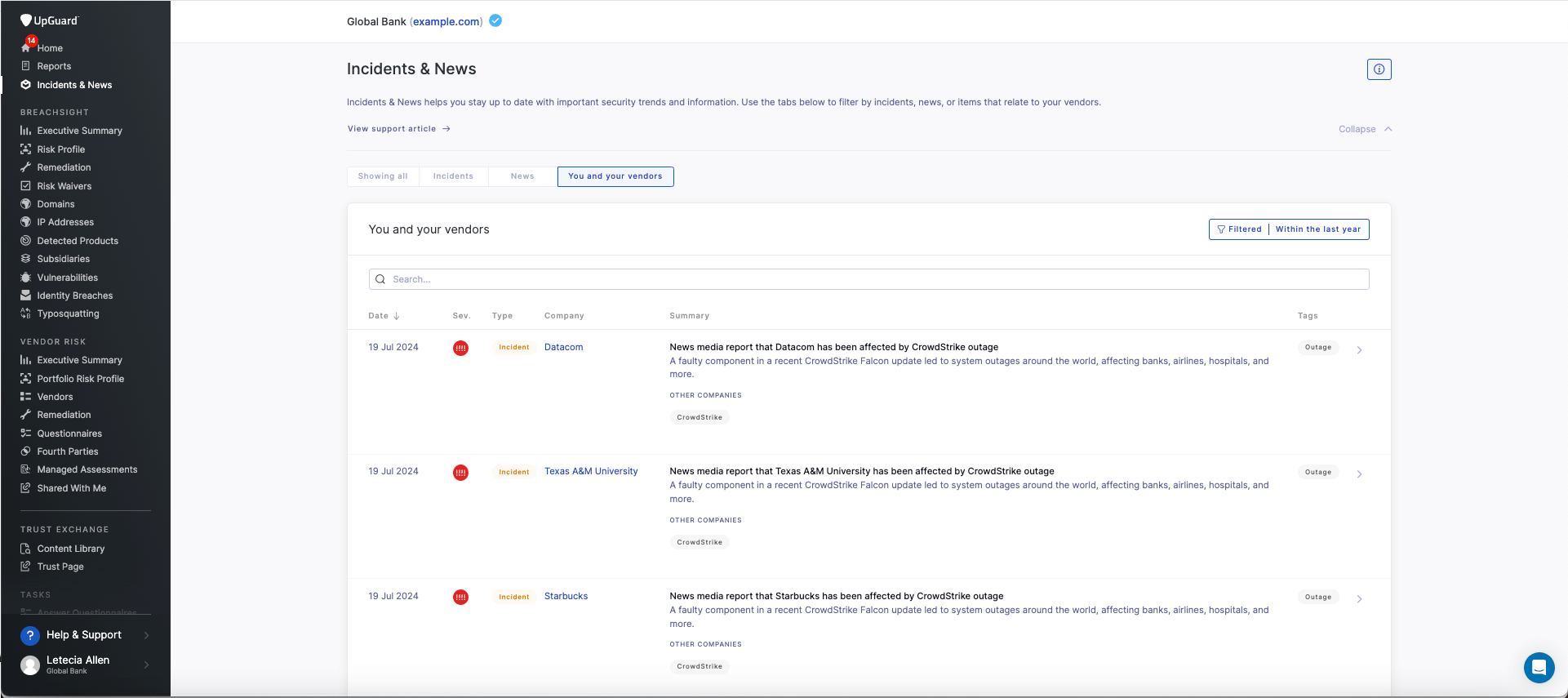
5. Breach detection and dark web monitoring
Breach detection and dark web monitoring identify compromised vendor data, leaked credentials, or exposed sensitive data on illicit online marketplaces, hacker forums, and underground data exchanges. Often, this functionality picks up leaked data and new breaches before companies publicly disclose them—allowing your organization to begin remediation efforts early.
Breach detection and dark web monitoring include:
- Detecting if a vendor has been breached before they publicly disclose it
- Identifying stolen credentials that could be used in credential-stuffing attacks
- Preventing unauthorized access by prompting password resets or additional security controls
6. AI-driven risk scoring
AI-driven risk scoring assigns dynamic security ratings to vendors based on threat exposure, security hygiene, and past incidents. Machine learning models analyze historical and real-time data to assess a vendor's potential risk at any given moment. Your organization can then use those risk profiles and scores to inform decisions about vendor relationships, service levels, and continuing specific partnerships.
AI-driven risk scoring includes:
- Providing a quantifiable risk metric to compare vendors objectively
- Adjusting in real-time as new threats or security changes are detected
- Prioritizing high-risk vendors for further review or remediation efforts
7. Regulatory compliance tracking
Regulatory compliance tracking monitors vendor security practices against established cybersecurity frameworks and regulations, such as GDPR, CCPA, NIST, ISO 27001, and DORA. Compliance tracking is especially vital for organizations in highly regulated industries, such as financial services and healthcare. Tracking regulatory requirements ensures vendors continuously meet compliance standards and reduce legal and financial risks.
Regulatory compliance tracking includes:
- Detecting non-compliant vendors before they cause regulatory penalties
- Automating compliance audits by continuously assessing vendor adherence to security controls
- Reducing the manual effort required for compliance management
8. Stakeholder reporting
With regulatory bodies increasing their emphasis on TPRM practices and global IT disruptions caused by third-party service becoming common, Senior management now expects to remain informed of the organization’s evolving vendor risk exposure. Vendor risk monitoring processes should naturally integrate into stakeholder reporting workflows, pulling vendor risk insights that actually matter to stakeholders, such as:
- The state of the organization’s security posture.
- A list of your most critical vendors with the highest potential of impacting the business during a security incident.
- Each vendor’s security posture changes over time.
- Risk treatment plans for newly onboarded critical vendors
Vendor risk monitoring reporting helps stakeholders make informed strategic decisions that align with the organization’s evolving third-party risk exposure.

9. Offboarding
Risk monitoring during offboarding helps compliance teams confirm all retired third-party services have had their access to internal sensitive resources revoked, a critical requirement of data privacy regulations such as the GDPR. An attack surface management tool could support this aspect of risk monitoring during offboarding by detecting regions in your digital footprint where connections to retired third-party services are still active.
Watch this video for an overview of attack surface management.
How often should ongoing monitoring happen in vendor risk management?
The frequency of ongoing vendor risk management (VRM) monitoring depends on several factors, including the nature of the business relationship, risk ratings associated with the vendor, and regulatory requirements. Here’s how you might determine the appropriate monitoring intervals:
- Vendor risk profile: High-risk vendors—those whose failure or breach could significantly impact your organization—should be monitored more frequently. Consider continuous, real-time monitoring for some aspects like cybersecurity risk or monthly to quarterly financial health and service delivery reviews.
- Regulatory requirements: Compliance with relevant regulations may dictate how often you monitor your vendors. For instance, vendors handling personal data may need to be reviewed more frequently due to data protection laws.
- Business impact: Vendors providing critical services or products in the supply chain, especially those directly affecting your core business functions or customer data, require more frequent monitoring. For example, IT service providers that handle sensitive data might need closer scrutiny than a supplier of office supplies.
- Vendor performance and history: Security teams should monitor vendors with a history of security incidents or inconsistent performance more frequently until they demonstrate stable improvement. Conversely, personnel might monitor vendors with a long track record of compliance and strong security posture less frequently, though still regularly.
- Changes in vendor status: Any significant changes in a vendor’s business—like risk criticality, mergers, acquisitions, financial distress, or leadership changes—should trigger more frequent monitoring to assess how these changes affect risk and compliance.
4 types of vendor risks that are Important to monitor
A vendor risk monitoring program typically addresses the following types of third-party risks.
- Information security risks: Third-party vulnerabilities and exposures that could increase your risk of being impacted should a vendor suffer a data breach. Continuous monitoring of third-party information security risks ensures vendors follow best security practices to safeguard the sensitive data you entrust to them.
- Concentration risks: Instances where a single vendor is responsible for the stability of your critical services, creating a single point of failure. Detecting concentration risks will encourage third-party service diversification and reduce the threat of critical disruptions during a significant global outage.
- Compliance and regulatory risks: Instances where a vendor fails to adhere to legal and regulatory requirements, increasing your risk of suffering a costly violation fine and legal actions.
- Reputational risks: The threat of a vendor’s actions or poor cybersecurity standards harming your organization’s public image. A vendor risk monitoring solution accounting for third-party reputational risks provides users with a continuously updating incident and news feed identifying all third-party services potentially impacted by a major security incident picked by the media.

Top vendor risk monitoring challenges in 2025
The following vendor risk monitoring challenges typically limit the efficiency of Vendor Risk Management programs.
1. Manual processes
Reliance on manual processes produces some of the most significant challenges to vendor risk monitoring. Some example manual processes limiting the impact of vendor risk monitoring include:
- Using spreadsheets to manage questionnaires
- Manual data entry of questionnaire responses
- Manually responding to repetitive questionnaires
- Tracking questionnaires and risk assessments with email follow-ups
These outdated manual practices create delayed risk monitoring practices that either completely overlook critical vendor risks or delay their remediation. Without upgrading manual processes to more modern processes leveraging automation technology, third-party risk oversight will only increase as the business scales.
The following video illustrates how automation technology could increase the efficiency and scalability of vendor risk monitoring processes.
Sign up to Trust Exchange by UpGuard for free >
2. Point-in-time assessments
Solely relying on point-in-time assessments limited vendor risk visibility to risk assessment schedules, providing a snapshot of your third-party risk exposure at a single time. This myopic approach to vendor risk monitoring fails to adapt to the dynamic nature of the vendor landscape, causing third-party risks arising between assessment schedules to be overlooked.
3. Insufficient data
Some vendor risk management programs adopt the poor practice of relying on vendor self-reported data received through completed questionnaires. Without an additional layer of verification provided by continuous monitoring processes, organizations could unknowingly be exposed to critical vendor security risks that will inevitably be exploited by cybercriminals.
Without independent verification of a vendor’s security posture through continuous monitoring, an organization operates under a false sense of security.
3. Unscalable VRM program
As an organization’s vendor ecosystem expands, managing vendor risks becomes more complex. Scaling risk monitoring efforts to account for hundreds or even thousands of third-party vendors, each with unique cyber risk factors and varying levels of criticality, could overwhelm even the most well-resourced Third-Party Risk Management teams.
Because vendor risk monitoring is a component of Vendor Risk Management, a scalable risk monitoring strategy can only be deployed on the foundation of a scalable VRM program, one that leverages automation technology to streamline all of the workflows in a Vendor Risk Management lifecycle.
Watch this video for some time-saving tips that will increase the efficiency of your Vendor Risk Management program.
Best practices for continuous monitoring in vendor risk management
Continuous monitoring is essential for managing vendor risks, ensuring that vendors meet contractual obligations, and complying with regulatory standards. Below are the best practices for optimizing vendor risk management through continuous monitoring.
Automating processes
Automating as much of the continuous monitoring process as possible improves efficiency and minimizes human error. By using a vendor risk monitoring solution and alert services, organizations can maintain a consistent overview of their vendor risk profiles.
Utilize software to automatically track performance metrics, compliance data, and risk indicators. Automation tools can also send alerts when vendors exceed predefined thresholds, enabling prompt corrective actions, saving time, and ensuring consistent data collection and analysis.
Tailoring monitoring efforts
It is essential to customize your monitoring efforts based on the specific risks associated with each vendor and their corresponding risk level. Vendors classified as high-risk, particularly those providing critical services, should be subjected to more frequent and thorough monitoring than those posing minimal risk.
Tailoring your approach in this manner allows for the effective allocation of resources, with a heightened focus on areas that could potentially significantly impact your business operations.
Regular reviews and updates
It is essential to establish a consistent schedule for reviewing your monitoring criteria, processes, and tools' effectiveness. Periodically update your risk assessments to reflect any changes in the vendor's business environment or your company’s risk tolerance, including implementing new tools and techniques for effective vendor monitoring.
This practice will ensure that your monitoring efforts remain relevant to the current industry standard and aligned with your organization’s unique needs and challenges.
Collaboration and communication
Foster a culture of strong collaboration and transparent communication among all parties involved in vendor management. Vendor management encompasses the procurement department, IT, compliance teams, and business units directly interacting with vendors.
Regular face-to-face meetings, video conferences, and shared digital platforms can play a pivotal role in ensuring everyone is well-informed about the monitoring standards and any issues the team has identified. This proactive approach will facilitate a coordinated and efficient response to any challenges.
UpGuard helps organizations collaborate and communicate with their vendors through our vendor collaboration streamlining services.
Compliance and reporting
Make sure you design your continuous monitoring activities to align with the specific regulations and industry standards applicable to your organization. Establish robust VRM reporting mechanisms that offer detailed insights and thorough documentation to substantiate compliance claims.
These measures are essential for successfully navigating regulatory audits and fortifying your organization's standing during contract negotiations or when renewing agreements with vendors.
Take advantage of always-on vendor management with UpGuard
UpGuard's Vendor Risk Management software is a TPRM platform designed to automate and streamline an organization’s third-party risk management program. Leveraging technology to simplify the often complex and time-consuming task of evaluating vendor risks helps organizations efficiently assess, monitor, and mitigate cyber risks associated with their vendors and suppliers.
Additional Vendor Risk features include:
- Customizable templates: UpGuard provides customizable questionnaire templates that users can tailor to meet specific industry standards, regulatory requirements, and organizational risk profiles.
- Bulk distribution and tracking: Vendor Risk enables the distribution of questionnaires to multiple vendors simultaneously and tracks the progress of each questionnaire, sending reminders and updates as necessary.
- Centralized vendor information: UpGuard centralizes all vendor information, including questionnaire responses, in a single platform, making it easier for organizations to access, review, and analyze vendor data.
- Automated risk scoring: UpGuard automatically scores vendors based on their questionnaire responses and other relevant data, which helps organizations quickly assess vendor risk levels and prioritize follow-up actions.
- Continuous monitoring: Vendor Risk monitors vendors’ cybersecurity postures and alerts users to changes or emerging vulnerabilities. Real-time visibility into vendor risks helps organizations respond swiftly to potential threats before they become incidents.
- Compliance management: UpGuard Vendor Risk helps vendors reach regulatory compliance with relevant regulations and standards (like GDPR, HIPAA, and SOC 2), tracking vendors’ certification statuses and identifying gaps or issues that need addressing.
- Collaborative features: Vendor Risk facilitates collaboration between internal teams and vendors, enabling seamless communication and efficiently resolving identified issues or risks.
- Comprehensive reporting: UpGuard provides detailed reports and dashboards that offer insights into the organization’s overall vendor risk landscape, which security teams can use for internal risk management purposes and to demonstrate compliance to stakeholders, auditors, and regulators.