Top Vendor Risk Monitoring Solutions for Continuous Oversight
Vendor risk monitoring software provides your organization with a continuous, data-driven view of third- and fourth-party security vulnerabilities, including open ports, leaked credentials, and misconfigured cloud storage buckets.
Detecting critical security changes as they occur empowers your team to act on verified threats early, preventing minor security drifts from escalating into major data breaches or compliance failures.
Learn how vendor risk monitoring fits into the broader Vendor Risk Management (VRM) process, discover the key features security teams need to choose effective Vendor Risk Management software, and compare the eight leading tools with guidance on which use cases they best support.
What is vendor risk monitoring?
Vendor risk monitoring is the continuous process of detecting and responding to changes in the security and compliance posture of third- and fourth-party vendors.
It closes the visibility gap between your periodic, point-in-time assessments by delivering a real-time, evidence-based view of each supplier’s attack surface. This provides the evidence your team needs to keep their risk profile accurate.
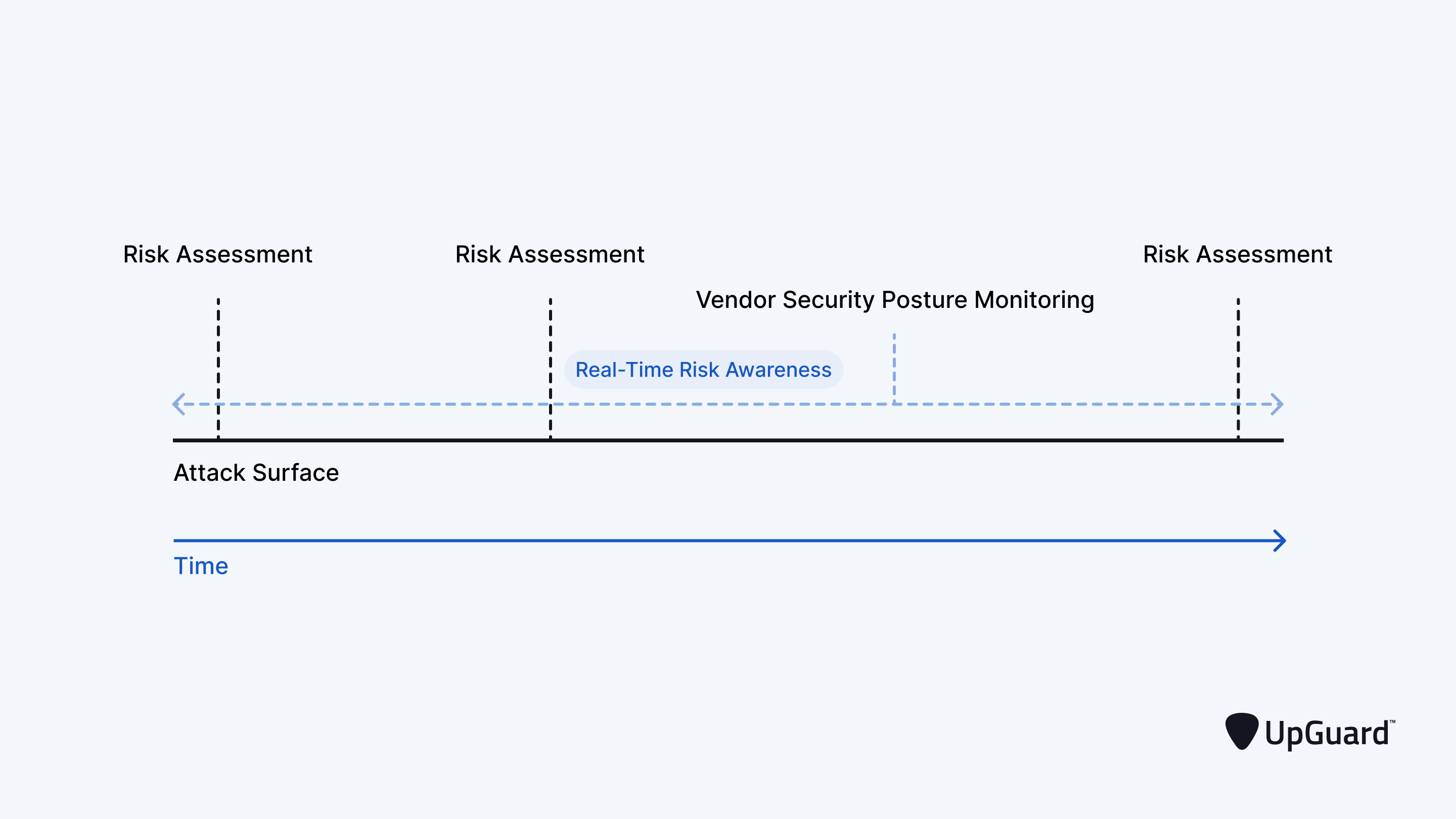
Vendor risk monitoring software supports the five key stages of Vendor Risk Management:
- Identification: Expedites the discovery of all the public-facing assets comprising a vendor's attack surface, giving security teams a baseline awareness of the depth of risk assessment each vendor requires.
- Risk assessment: Automatically highlights security control and compliance gaps, expediting risk assessment completions and remediation responses.
- Monitoring: Tracks emerging risks impacting a vendor's security posture on an ongoing basis.
- Mitigation: Delivers actionable (ideally real-time) evidence when a risk is detected. This lets your organization quickly communicate remediation requirements to vendors and enforce remediation timelines in Service Level Agreements (SLAs).
- Continuous improvement: Aggregates and analyzes historical risk and remediation data, helping your security team identify trends such as recurring vulnerabilities and refine risk models and assessment cadences.
Do a deep dive into our vendor risk management overview here.
Features of an ideal vendor risk monitoring solution
There’s a wide range of vendor monitoring and management tools on the market. When selecting a platform for your organization, check for the following features:
1. Real-time risk alerts
Select a platform that sends automatic notifications when monitoring detects a material change, like:
- Changes to your security rating
- Updates to vendors' security ratings
- Information on new identity breaches
This gives your team a critical time advantage, allowing them to investigate and contain a threat before it escalates into a damaging breach or a costly compliance failure.
2. Continuous monitoring
A core function of any effective TPRM software is automatically rescanning each vendor’s internet-facing infrastructure on a rolling, near-real-time basis, flagging issues like:
- Insecure or expired SSL/TLS certificates
- Missing or unavailable SSL
- SPF, DKIM, and DMARC settings
- HTTP Strict Transport Security (HSTS)
- Email spoofing and phishing risk
- Common Vulnerabilities and Exposures (CVEs)
By comparing fresh findings to the last validated assessment, your security team can spot configuration drift and launch a remediation workflow. No waiting weeks or months for the next scheduled review.
3. Automated risk scoring
Automated risk scoring uses data from continuous monitoring to rank and quantify each vendor's security posture. A vendor risk monitoring solution should also continuously update vendor security scores using external scan results, data leak signals, domain hygiene checks, and other security signals.
Look for a platform with a scoring process that:
- Refreshes vendor risk scores daily
- Ranks findings by severity and asset criticality
- Breaks down vendor security scores into transparent categories, like network hygiene, DNS hygiene, data leak signals, brand reputation, and cloud-security posture
Read more here on how to conduct a comprehensive vendor risk assessment.
A category-level breakdown exposes hidden risks even when the headline score looks acceptable. This helps you decide which risks you can tolerate and which demand immediate attention.

4. Integration with internal systems
An effective platform should integrate smoothly with your existing security ecosystem using its APIs and webhooks to push information into other apps like ticketing systems (Jira, ServiceNow), GRC platforms, or SIEMs. This allows you to embed Vendor Risk Management workflows more easily into your organization’s workflows, resolving visibility issues caused by departmental data silos.
With an effective vendor risk monitoring tool integration, you can:
- Create an incident or task in your ticketing system (e.g., Jira or ServiceNow) when a critical issue arises.
- Log a time-stamped audit trail of every remediation step (without manual re-entry) on the platform and, for example, your central GRC system.
- Push real-time notifications to colleagues and stakeholders via communication platforms, like Slack or Teams.
5. Single source of truth
The right vendor risk monitoring tool gives you a central, permission-controlled repository for every vendor, including records of their:
- Risk waivers created, modified, or deleted
- Evidence additions, deletions, and updates
- Vendor tier definitions and assignments
Centralizing your vendor risk data calms the chaos of searching through scattered emails and spreadsheets while preparing for an audit. Your team works from a single source of truth, ensuring complete visibility, streamlined collaboration, and nothing slipping through the cracks.
6. Automated remediation workflows
Automated vendor risk remediation is a key part of many TRPM solutions. When vendor monitoring detects an issue, like an open RDP port or an expired TLS certificate, the platform should:
- Create a pre-filled remediation ticket with asset details, severity, and recommended fixes.
- Assign a remediation deadline based on the SLAs defined in your risk policy.
- Notify the right internal owner and, where appropriate, the vendor.
- Track the fix through to resolution and close the ticket once verified.
Replacing ad hoc emails with this structured, auditable workflow helps teams respond to vendor cyber risks faster and prove due diligence during audits.
7. Fourth-party vendor risk monitoring
Your vendor’s security is only as strong as its suppliers. A troubling 84% of financial firms have been exposed to a breach as a result of a fourth-party risk—an incident where an external party is compromised because their own vendor is breached.
Look for a platform to discover and map the fourth-party network's dependencies. This visibility can help you spot hidden risks in the supply chain that wouldn't show up in a standard questionnaire or assessment.
Watch this video to learn how UpGuard detects obscure technologies in your digital footprint.
8. Stakeholder reporting capabilities
Effective reporting is a key aspect in presenting and justifying VRM programs to leaders, stakeholders, and regulators. Choose a vendor risk monitoring platform that generates timely and accurate:
- Board-level summaries of the overall risk landscape
- Detailed vendor risk profiles (including remediation actions)
- Compliance and regulatory reports
- Supply chain impact assessments
This level of reporting helps you align your risk, security, and procurement teams while also giving senior stakeholders the confidence to support your Vendor Risk Management recommendations.
9. Automated regulatory compliance risk monitoring
Choose a platform that tracks each vendor’s compliance with the specific standards your organization must meet, such as GDPR, ISO 27001, or PCI DSS.
Look for capabilities that identify issues like expired certificates and map them to relevant compliance failures, such as a violation of a critical PCI DSS control.
By aligning a vendor risk monitoring solution with your internal security frameworks, your team can assess and address third-party risks using the same regulatory lens you apply internally.
8 top vendor risk monitoring software solutions for your organization
Below, find concise summaries of eight of the leading Vendor Risk Management programs:
1. UpGuard (voted #1 leader in TPRM)

Core capabilities
- Daily security scores: UpGuard refreshes its security scores daily, giving you near real-time visibility into each vendor’s evolving risk profile. Unlike competitors that may take weeks to reflect changes, UpGuard accounts for remediation efforts almost instantly, so you're never working with outdated information.
- Vendor risk AI: UpGuard’s AI automates questionnaire analysis and security document review, mapping findings to relevant security controls in seconds. It can assess up to 90% of controls from a single file and generate risk reports instantly, freeing analysts to focus on the more strategic aspects of Vendor Risk Management.
- Fourth-party vendor risk monitoring: UpGuard reveals the hidden dependencies between your vendors and their suppliers (fourth parties), highlighting vulnerability and concentration risks that standard assessments often miss.
- Stakeholder reporting tools: UpGuard uses customized reporting templates to share compliance status, security posture changes, and critical metrics with executives and boards. You’ll have tangible evidence to support informed risk management decisions.
Ideal use case
UpGuard is ideal for larger companies seeking a scalable solution with a quick initial setup. Its shallow learning curve also makes it accessible for non-technical teams.
Integrations
UpGuard connects with over 4,000 applications via Zapier and has native integrations with tools including Jira, ServiceNow, and Slack. It also offers a well-documented API for custom work for end-to-end workflow management.
2. SecurityScorecard
See how UpGuard compares with SecurityScorecard >
Core capabilities
- Risk signal sources: SecurityScorecard uses a mix of open, proprietary, and dark web monitoring risk signals to spot external threats and weaknesses in a vendor’s attack surface.
- Vendor lifecycle monitoring: The Atlas plug-in supports risk monitoring and questionnaire automation integrations (a separate license is required and may cause workflow disruptions).
- Compliance framework tracking: The platform maps security questionnaires to frameworks—like ISO 27001, PCI DSS, and NIST CSF—and shows real-time progress for each sent questionnaire via the dashboard.
Ideal use case
SecurityScorecard is suitable for large enterprises requiring a high-level overview of third-party vendor risk exposure for executive-level reporting.
Integrations
SecurityScorecard connects to various GRC and security platforms, such as RSA Archer and ServiceNow.
SecurityScorecard’s questionnaire module, Atlas, is a separate product that requires its own license. This separation can create disjointed workflows between a vendor's security rating and their questionnaire assessments.

3. Bitsight
See how UpGuard compares with Bitsight >
Core capabilities
- Future forecasting: Bitsight analyzes multiple botnets, malware, and other threat intelligence sources to assess current vendor risk ratings and likely future vendor performance.
- Fourth-party monitoring: The platform flags automatic downstream vendor and supply chain detection that could disrupt business continuity if a hacker compromised your information security.
- Advanced reporting: You can generate data-driven reports on your vendor ecosystem risks and emerging threats to support high-stakes decisions (charged separately).
Ideal use case
Bitsight is an option for complex businesses, especially in finance and insurance, where regulation and compliance require evidence-based risk insights and analytical forecasting of security performance.
Integrations
Bitsight connects to GRC, TPRM, and SOAR tools like ServiceNow, Jira, Splunk, and Power BI. Its limited API supports custom reporting and specific automation tasks. Some workflows require add-ons or separate modules.
Key capabilities, such as advanced reporting and detailed risk forensics, are often licensed as separate add-on modules. This can increase the total cost of ownership and silo critical data from core workflows.

4. OneTrust
See how UpGuard compares with OneTrust >
Core capabilities
- Streamlined onboarding: Automated GRC tools handle your vendor onboarding, risk assessments, and due diligence processes.
- Regulatory compliance coverage: The platform supports all major compliance frameworks, including stricter EMEA standards, with analyst support available for complex tasks.
- Targeted reporting: OneTrust delivers detailed analysis for organizations monitoring risks across various categories, including ESG and data privacy.
Ideal use case
OneTrust may be suitable for companies needing a Vendor Risk Management solution as part of the extensive customization of risk and compliance processes, integrated into a broader privacy, ethics, and compliance framework.
Integrations
OneTrust includes pre-built integrations with platforms like RSA Archer and ServiceNow and an open API for linking to GRC, HR, and other internal tools.
OneTrust does not offer users external risk visibility, which significantly limits the platform’s risk monitoring capabilities. It also doesn’t detect fourth-party risks natively.

5. Black Kite
Learn how UpGuard compares with Black Kite >
Core capabilities
- Security score costing: The platform assigns A–F risk grades using OSINT data and estimates the financial impact of each potential vendor breach.
- Smart compliance mapping: Black Kite’s “Bridge” module automatically contacts vendors to help them fix the issue of concern.
- Nth-party supply chain monitoring: The software identifies supply chain security and concentration risks, providing advanced awareness of potential operational disruptions on Black Kite’s dashboard.
Black Kite customers who want to implement a risk assessment workflow must consider integration options with separate third-party risk management platforms.
Ideal use case
Black Kite is geared toward firms that work to understand the financial impact of third-party cyber risks and value risk quantification based on the Open FAIR™ standard.
Integrations
Information on Black Kite’s external integrations is limited, but its AI document scanning requires integration with a separate TPRM solution to connect to assessment workflows.

6. RiskRecon
See how UpGuard compares with RiskRecon >
Core capabilities
- Asset-based scoring: RiskRecon ranks vulnerabilities based on the threat itself and the value of an asset, using an A–F score.
- Fourth-party detection: The platform detects fourth-party technologies to help users see the potential impact of complex risks based on vendors’ supply chains
- Detailed analytics: You can run a wider range of reports on simple and complex internal and external risks with detailed remediation guidelines for IT teams.
RiskRecon does not offer an integrated risk assessment workflow. It also doesn’t support vendor risk monitoring during the onboarding and continuous monitoring phases of the VRM lifecycle
Ideal use case
RiskRecon, a Mastercard company, aims its services at IT-centric businesses that need detailed asset discovery and vulnerability prioritization based on the value of assets.
Integrations
RiskRecon’s technology partners include AWS, RSA Archer GRC, Nteros, and Smarsh.

7. Panorays
See how UpGuard compares with Panorays >
Core capabilities
- Features for financial firms: Panorays maps to mainstream and nuanced frameworks, including ISO 27001, PCI DSS, and NYDFS 500, ideal for firms with complex financial risk monitoring requirements.
- Whole lifecycle monitoring: The platform supports the entire VRM lifecycle, applying its risk monitoring tools to each stage to share details on internal and external risk exposures.
- Stakeholder reporting capabilities: Users can create executive-level reporting templates and recommended remediation actions.
Ideal use case
Panorays is best for businesses that want simplified vendor onboarding and assessments with automated questionnaires. It also offers clear security ratings based on external scans and security details the vendor provides.
Integrations
Panorays’ technology partners include RSA Archer and ServiceNow, and you can integrate others through its JSON-based REST API.
Panorays doesn’t release technical information on the sources it consults to determine security scores

8. Vanta
See how UpGuard compares with Vanta >
Core capabilities
- Advanced onboarding: The platform automates evidence collection across 35+ compliance frameworks, including questionnaires and documentation requests.
- Regulatory compliance risk monitoring: Vanta automates and streamlines regulatory compliance monitoring and sends real-time alerts when a supplier drifts out of line.
- Stakeholder reporting capabilities: You can generate detailed stakeholder reports with complex compliance metrics on regulatory, financial, operational, and IT issues.
You’ll need plug-ins to detect and monitor vendor security ratings, threat intelligence, and security postures. Vanta does not provide fourth-party detection or Vendor Risk Management natively.
Ideal use case
Vanta is ideal for organizations focused on automating compliance.
Integrations
Vanta has pre-built integrations with common cloud providers, HR Information Systems (HRIS), and project management tools. The API also allows for deeper data integration.

Automate vendor risk monitoring and scoring with UpGuard
Researchers uncover a new cybersecurity threat every 17 minutes. Data privacy laws are increasing in number and reach every year in the US and worldwide.
UpGuard offers end-to-end security from onboarding and contract renewal right through to offboarding. Our platform provides a complete view of your vendor ecosystem through real-time monitoring, automated risk scoring, and clear reporting.