Cybersecurity is becoming a growing priority for organizations, as daily news headlines feature large-scale data breaches due to unauthorized access and ransomware attacks dismantling systems across the globe. The last thing an organization wants is to become the next headline because its poor cybersecurity posture left it vulnerable to hackers.
Cybersecurity audits meticulously analyze and report on an organization’s security program, helping them identify weak points that need addressing. Audits can require considerable time and energy, which is where cybersecurity auditing tools can help—navigating network structures and system configurations while ensuring compliance with regulatory and policy frameworks.
If your organization is in the market to reduce your cybersecurity risk, read more about the purpose and importance of regular cybersecurity audits and the top three features to look for in auditing tools.
What is a Cybersecurity Audit?
A cybersecurity audit is a systematic and measurable technical assessment of how an organization implements its cybersecurity policies, procedures, and systems. This critical examination focuses on evaluating the effectiveness of an entity's information systems in terms of confidentiality, integrity, and data security. Internal audits and external audits can both accomplish these goals.
These audits examine various aspects of an organization’s security posture, including network and operating systems, data protection and encryption methods, malware protection, firewall configurations, antivirus software, and user access controls. Additionally, these audits assess compliance with relevant regulatory frameworks and standards, such as GDPR or HIPAA, ensuring that the organization complies with legal and best-practice requirements.
The goal is to identify vulnerabilities, non-compliances, and potential improvements in the current cybersecurity setup, protecting the organization against potential threats and data breaches while ensuring regulatory compliance. This process usually involves automated tools and manual assessments, enabling a comprehensive evaluation of the organization's network security, vulnerability management, and digital security posture.
Audits vs Assessments
Cybersecurity audits and assessments share many similarities, like assessing an organization’s information security infrastructure to identify potential vulnerabilities.
The main difference is how those findings are used. In an assessment, those findings are often compared against a standard, like cybersecurity compliances or regulations, and identify if an organization meets those requirements. If these risk assessments are met, that organization can promote that they are “XZY-Compliant” or meet the standards of “XYZ Regulation.”
In an audit, those findings are used to determine whether the existing security measures are effective for the organization. Audits determine if the organization has sufficient cyber policies like incidence response, IT team responsibilities, cyber maturity, adequate controls, etc. Organizations can also use frameworks to structure their audits.
In combination, these processes help organizations defend against cybersecurity threats holistically and mitigate the risks associated with those threats.
How Do You Perform a Cybersecurity Audit?
Including regular cybersecurity audits in your company's information security policy (ISP) and broader enterprise risk management (ERM) framework is important. A well-defined process for audit teams to conduct a cybersecurity assessment ensures that the audits focus only on recent and high-risk threats rather than a backlog of outstanding IT security issues. This helps identify and mitigate the potential risk factors for your company's security.
Here are three steps to perform a cybersecurity audit in your organization:
1. Determine Scope
To conduct a cybersecurity audit, begin by defining its scope. Determine critical elements of your cybersecurity program to be assessed and understand the audit process's why, who, and how. Focus areas include IT infrastructure, sensitive data handling, an organization’s physical security, cybersecurity policies, and compliance with relevant standards.
Ensuring you document the audit requirements facilitates consistency in future evaluations. In the context of compliance audits, it's essential to understand and comply with specific regulatory requirements and acknowledge the potential need for external audits.
2. Threat Detection
The next step in a cybersecurity audit involves identifying and analyzing threats and evaluating security controls to neutralize them. Prevalent cyber threats include DDoS attacks, various forms of malware like ransomware, Shadow IT practices, social engineering phishing, stolen passwords from past data leaks, cross-site scripting, SQL injections, and zero-day exploits.
Continuous security monitoring, possibly through an automated attack surface management platform like UpGuard, facilitates real-time detection of cyber threats, enabling security teams to address them proactively before they can be exploited.
3. Plan Response
After identifying threats to an organization's cybersecurity, the next step is to implement an organization’s incident response plan. Utilize the audit report to inform your incident response plan, which includes a methodology for risk prioritization and remediation processes, a business continuity plan for disaster recovery, documentation of all tools aimed at preventing, detecting, and responding to threats, and a communication plan that includes employee training and awareness initiatives.
A clear incident response plan mitigates risks and facilitates a smoother audit process by showcasing the current proactive cybersecurity measures.
Types of Cybersecurity Auditing Tools
Cybersecurity auditing tools serve various purposes, inspecting all potential vulnerabilities and safeguarding against threats. These can be on-premise network security auditing tools and cloud-based SaaS tools. Some cybersecurity auditing tools include:
- Vulnerability Assessment Tools: Evaluates systems for known vulnerabilities, providing insights into weak points within an IT infrastructure. One example of this is Nmap, an open-source tool that helps with network discovery, management, and monitoring
- Penetration Testing Tools: Also referred to as “pen-testing,” this tool mimics cyber attack scenarios to evaluate cybersecurity posture. One example of this is Metasploit, a powerful framework for exploiting vulnerabilities, security testing, and identifying mitigation strategies
- Security Information and Event Management (SIEM) Tools: Aggregates and analyzes event data from endpoints to provide a consolidated view of information security, detecting activities that might indicate a data breach or other threat
- Intrusion Detection and Prevention Systems (IDPS): Actively monitors networks and systems for malicious activities, blocking and preventing issues as they are discovered
- Web Application Security Scanners: Scruntizes web applications for known security vulnerabilities while working with developers to identify problematic coding practices
- Compliance Management Tools: Ensures cybersecurity policies, practices, and controls adhere to regulations and standards, validating compliance with popular frameworks (GDPR, HIPAA, PCI DSS, etc.)
- Endpoint Security Tools: Protects network endpoints (user devices, servers, network devices) from malicious activity by securing the network and ensuring connected devices have predefined security standards
- Security Configuration Management (SCM) Tools: Ensures configurations and maintains system integrity throughout an IT system’s lifecycle, aligning with security policies and addressing non-compliant systems
- Incident Response Tools: Manages and mitigates security incidents and breaches, including incident detection, investigation, and response
Top 3 Features of Cybersecurity Auditing Tools
Cybersecurity auditing tools include various features that help organizations identify their current cybersecurity posture and what they can do to improve. Organizations may have unique needs and pain points that specific cybersecurity auditing providers can address, and you should choose the one that best fits your organization’s overall goals and current systems (i.e., Windows). However, all cybersecurity auditing tools should include the following features.
1. Comprehensive Vulnerability Detection and Analysis
Detecting and analyzing vulnerabilities is an absolute must-have feature for cybersecurity auditing tools. A tool should include a vulnerability scanner that provides a thorough, holistic, and multi-dimensional approach to identifying, examining, and understanding vulnerabilities across an organization’s digital landscape. Additionally, comprehensive vulnerability detection and analysis should provide:
- Depth and Breadth of Scanning: Vulnerability scans should occur across the entire network, systems, apps, and assets, covering vulnerabilities like misconfiguration, software flaws, and insecure settings
- Detailing Reporting: Insights, vulnerability severity ranking, and remediation guidance should be available via reports to different organizational roles
- Continuous Monitoring and Scanning: Networks should be continuously monitored with scheduled and automated scans to identify and assess risks and changes in security posture
How UpGuard Can Help
UpGuard Breach Risk is an all-in-one external attack surface management tool that provides comprehensive vulnerability detection and analysis.
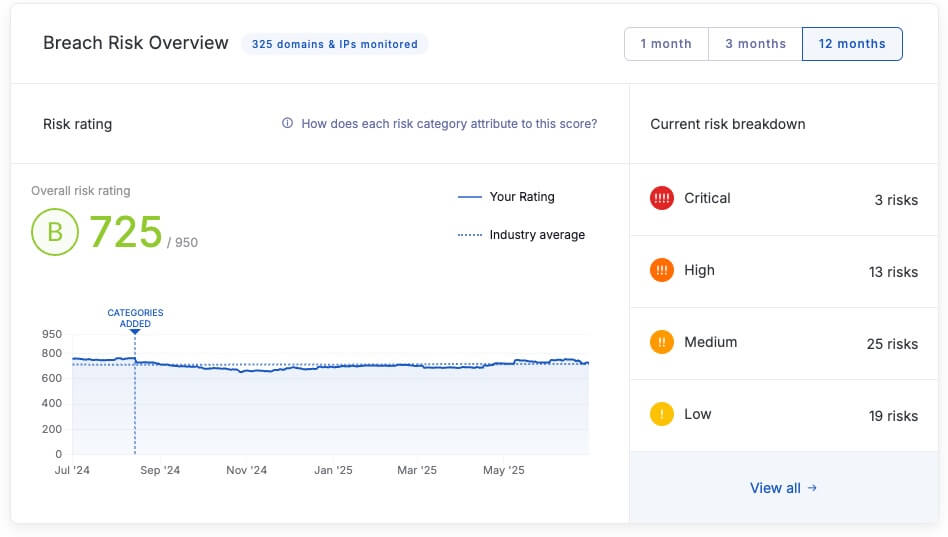
Reduce your attack surface as Breach Risk discovers vulnerabilities that may be exploitable in the software running on your websites. Our Reports Library provides executive reporting and report templates detailing risks across domains, IPs, and categories. Also, Breach Risk’s continuous security monitoring provides real-time information about recent security incidents, risk profiles, domains & IPs, and asset portfolios.
2. Compliance Management and Reporting
A comprehensive cybersecurity tool should automate vulnerability detection and analysis and use those findings to assess compliance with cybersecurity regulations and frameworks. This includes:
- Regulatory Compliance Assurance: Ability to assess, monitor, and report on the compliance status of the organization with relevant regulatory standards like GDPR, HIPAA, PCI DSS, etc
- Customizable Compliance Frameworks: Flexibility to adapt to different compliance frameworks and standards relevant to the specific industry and region
- Audit Trails and Forensic Capabilities: Maintain logs and records of activities, configurations, and changes for audit trails and forensic analysis, with the capability to reconstruct events to understand the what, how, and when of potential security incidents
How UpGuard Can Help
UpGuard Breach Risk helps your organization comply with cyber regulations and frameworks through our security ratings based on industry-standard best practices, standards, and frameworks.

Our security questionnaire library also speeds up your cybersecurity audit process by providing deeper insights into existing security structures. Utilize our industry-leading questionnaires, or build your own from scratch. Examples from our questionnaire library include the NIST Cybersecurity Framework, the Health Insurance Portability and Accountability Act (HIPAA), ISO 27001, Essential Eight, and more.
3. Real-Time Alerting and Notification
Cybersecurity concerns are a time-sensitive issue. With every passing minute, the chances of a malicious actor taking advantage of an exposed digital vulnerability increase. That’s why a cybersecurity audit tool that provides real-time alerting and notification is so important—if your organization can address vulnerabilities or incidents as soon as they occur, you reduce the incident's overall impact and can recover faster. This feature can include:
- Proactive Alerting: Instant alerts for identified vulnerabilities or incidents and customizable alert parameters to prioritize notifications based on severity and relevance
- Automated Response: Automated actions in response to identified threats or vulnerabilities, like isolating a compromised system in the vent of a malware attack
How UpGuard Can Help
UpGuard Breach Risk features a host of default notifications and allows you to create and manage custom notifications. Get notified if your security score drops, and utilize continuous security monitoring for real-time risk insights.

Additionally, our workflows and waivers allow your organization to simplify and accelerate how you remediate issues, waive risks, and respond to security queries. Stay informed about risks and utilize our workflows to track progress—knowing immediately when issues are fixed.