Tracking cybersecurity metrics is no longer just a best practice—it is essential. From protecting sensitive data to preventing devasting data breaches and spotting cybersecurity risks, having a clear set of key performance indicators (KPIs) can make all the difference. These KPIs help organizations determine the effectiveness of their cybersecurity measures and drive informed decision-making.
However, despite growing digital risks, PWC reports that only 22% of CEOs feel confident that their risk exposure data is comprehensive enough for sound design-making. Alarmingly, this statistic hasn’t budged in the last decade. Additionally, the EY Global Information Security Survey reveals that just 15% of organizations are confident their InfoSec reporting fully meets their expectations.
This blog outlines the critical cybersecurity metrics your organization should track to manage vendor risk better, strengthen defenses, and stay ahead of evolving threats.
What are cybersecurity metrics?
Tracking cybersecurity performance starts with understanding the fundamental components: metrics, Key Performance Indicators (KPIs), and Key Risk Indicators (KRIs). These measurable values provide the necessary data to assess the efficiency of your security program, allowing you to move from guesswork to a data-driven security strategy.
Defining Terms
- Cybersecurity metrics (The "what"): These are the foundational, measurable data points that provide a snapshot of your current cybersecurity posture. They track the health and effectiveness of security controls and processes.
- Example: The sheer volume of security alerts generated by your Security Information and Event Management (SIEM) system in a single week.
- Example: The sheer volume of security alerts generated by your Security Information and Event Management (SIEM) system in a single week.
- Key performance indicators (KPIs) (The "how"): These are strategic, rate-based measurements tied to high-level security goals and business outcomes. They show how well your security practices are performing against specific objectives.
- Example: Mean Time to Resolve (MTTR) a security incident, which directly measures your response efficiency and its impact on business continuity.
- Key risk indicators (KRIs) (The "before"): These metrics focus specifically on risk exposure and help pinpoint potential vulnerabilities before they become successful security incidents. Monitoring KRIs allows you to initiate quick remedial action to prevent a cyber threat from escalating.
- Example: The number of failed login attempts across your network or the total Vulnerability Exposure Time (how long a critical flaw has been unpatched)
Click here to learn more about the key cybersecurity metrics >
Clarifying the difference
The distinction between metrics and KPIs often lies in their strategic value to the business:
Why do cybersecurity metrics matter?
Whether you’re tracking incident response times, vendor risk ratings, or employee security training completion rates, the right cybersecurity metrics and KPIs empower you to make informed decisions and prove the value of your security investments.
Information security metrics transform raw data into actionable insights. Metrics provide visibility into an organization’s vulnerabilities, strengths, and weaknesses—allowing you to make data-driven decisions. As Peter Drucker said, what gets measured gets managed, and cybersecurity is no different. If you can't measure your security efforts, you won't know how you're tracking.
The core impact on security posture
Metrics directly improve your security posture in several critical ways:
- Financial justification (ROI): Metrics are essential for demonstrating the Return on Investment (ROI) of security tools and projects to stakeholders. They translate technical risks into financial impact, which justifies budget increases.
- Rapid improvement of incident response: Measuring timeliness KPIs like Mean Time to Contain (MTTC) or Mean Time to Respond (MTTR) identifies bottlenecks and drives automation, directly improving your organization’s resilience. Quicker containment limits the damage and scope of an attack.
- Proactive risk reduction: Key Risk Indicators (KRIs) help detect potential issues before they become full-blown incidents, such as tracking the risk profile of critical digital assets.
- Effective prioritization: Metrics help security teams prioritize remediation efforts based on the severity and exploitability of vulnerabilities, rather than simply addressing the highest volume of alerts.
Regulatory compliance and governance
In a world of increasing regulatory scrutiny (like GDPR, HIPAA, and NIST), metrics provide the necessary evidence to prove diligence and compliance:
- Compliance adherence rate: This metric tracks the percentage of regulatory requirements and internal security policies that your organization meets over a period.
- Audit readiness: Metrics provide auditable evidence of control effectiveness, which is crucial for GRC (Governance, Risk, and Compliance) efforts. For example, showing a high Patch Compliance Rate demonstrates adherence to mandates requiring timely vulnerability remediation.
Key benefits summarized
Choosing and tracking the right metrics allows organizations to:
- Bridge the communication gap: Translate technical jargon (e.g., "33 million firewall blocks") into business-relevant concerns like financial loss, brand reputation, and competitive standing for board members.
- Enable benchmarking: Compare the organization’s performance (e.g., security score) against industry peers and historical trends to highlight areas for improvement.
- Set clear risk alignment: Ensure that security efforts and resources are aligned with the Board's defined risk appetite and tolerance levels.
- Justify automation: Metrics like reduced Mean Time to Respond (MTTR) or a lower volume of manual security tickets prove the value of investing in Security Orchestration, Automation, and Response (SOAR) technologies.
Categories of cybersecurity metrics
Effective cybersecurity reporting requires organizing your metrics into clear, distinct categories. This structure prevents "data noise," ensures the right level of detail reaches the right audience (from SOC analysts to the Board), and aligns security performance with business objectives.
Here are the four essential categories for modern security reporting:
1. Operational metrics (The SOC view)
These focus on the day-to-day efficiency and speed of your security operations. They are crucial for Security Operations Center (SOC) teams to measure efficiency, prioritize resource allocation, and optimize automated responses.
2. Strategic metrics (The board view)
These KPIs translate technical performance into quantifiable business risk, financial impact, and program maturity. They are designed for the C-suite and Board to inform strategic alignment and investment decisions.
3. Compliance metrics (The GRC View)
These focus on demonstrating adherence to internal policies, regulatory requirements, and control frameworks (like NIST, ISO 27001, or GDPR).
- Compliance adherence rate: The percentage of regulatory or policy requirements met within a given period.
- Audit pass rate: The success rate of internal or external security audits, showing that tools and procedures are working.
- Unremediated high-risk audit findings: The count of critical vulnerabilities or control gaps identified in the last audit that remain open beyond the recommended remediation timeframe (e.g., > 90 days).
4. Vendor risk management (VRM) metrics (The third-party view)
These manage the risk introduced by third-party vendors and the extended supply chain. As breaches increasingly originate from external partners, these metrics are vital for continuous risk monitoring.
- Average vendor security rating: The composite external security score reflecting the cyber health of your third-party ecosystem.
- Mean time for vendor incident response (MTTVR): How quickly a vendor acknowledges and starts to contain a security incident or vulnerability reported by your team.
- Percentage of vendors with valid certifications: The ratio of high-risk vendors that have provided or maintained required documentation (e.g., SOC 2, ISO 27001).
Top cybersecurity metrics & KPIs for modern security
The security landscape is constantly evolving, requiring modern security teams to track metrics that go beyond simple vulnerability counts. The following KPIs and metrics focus on timeliness, risk exposure, and the critical financial impact of security efforts.
For reference, explore our cybersecurity metrics checklist here >
Operational timeliness and efficiency
These KPIs are essential for measuring the efficiency of your security team and its deployed technologies.
The human factor
User behavior remains a top entry point for attackers, making it vital to measure the effectiveness of employee security awareness.
- Phishing click-through rate: The percentage of employees who click on a simulated phishing link or submit credentials. A high rate justifies increased security awareness investment.
- User awareness level: Measured by security quiz scores, self-assessment confidence ratings, and tracking employee engagement during training.
Vendor risk management (VRM) KPIs
Third-party breaches are a major source of compromise, requiring dedicated KPIs to manage the extended supply chain risk.
- Average vendor security rating: A quantified, external score that reflects the overall security posture and cyber health of your third-party ecosystem.
- Percentage of vendors with valid certifications: The ratio of high-risk vendors that have provided up-to-date and valid compliance certifications (e.g., SOC 2, ISO 27001).
- Mean time for vendor incident response (MTTVR): Tracks how quickly a third-party partner acknowledges and begins remediation for a vulnerability or incident you have identified in their environment.
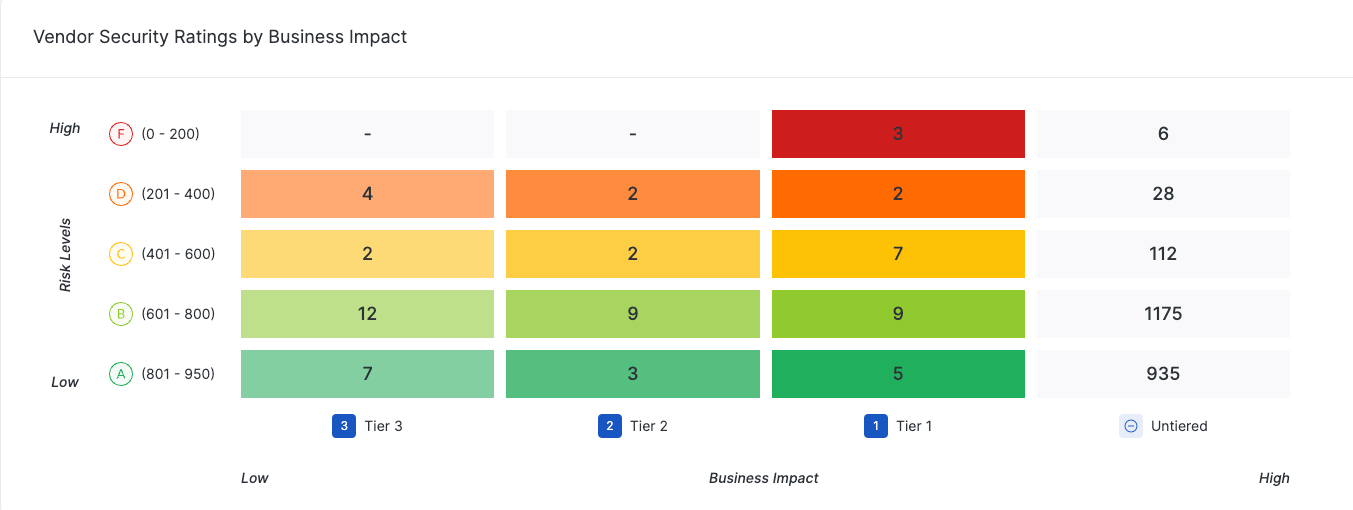
UpGuard’s Vendor Tiering feature allows third-party vendors to be tiered based on security criticality. This allows vendors with the highest potential impact on your security posture to be prioritized in monitoring and remediation processes, reducing the likelihood and impact of third-party breaches.
Cost-related KPIs (The financial impact)
These metrics are the language of the boardroom, showing the financial risk and the value of security investments.
How to build a cybersecurity metrics dashboard
A powerful cybersecurity dashboard transforms scattered metrics into a compelling, coherent narrative. It is the most effective tool for communicating security status to different stakeholders.
Here is a step-by-step guide to building an effective, customizable dashboard:
Step 1: Define your audience and their story
The first and most crucial step is to define the purpose and audience for the dashboard. A one-size-fits-all dashboard will fail both the SOC team and the Board.
- For the board/executive: The story should focus on strategic concerns: risk trends, financial impact, and compliance adherence. Use KPIs like Quantified Risk Exposure and Security Posture Score.
- For the SOC/operational team: The story should focus on efficiency: triage volume, response speed, and infrastructure health. Use metrics like Alert-to-Incident Conversion Rate and MTTD/MTTR.
Step 2: Select critical metrics and KPIs
Once the story is defined, select a small, critical set of data points. Avoid information overload; focus on 7-8 concrete, understandable, and actionable data points per dashboard view.
- Focus on Trends: Always display metrics to show change over time, enabling the audience to discern whether performance is improving or declining.
- Prioritize Actionability: Operational dashboards should highlight metrics that, when trending negatively (e.g., rising patch latency), require an immediate change in security team action.
Step 3: Establish data sources and extraction
Consolidation is priority number one for any effective dashboard. You need a single view of network security without scrolling or switching between apps.
- Integration is key: Identify how to pull data from your different security platforms (e.g., SIEM, EDR, Vulnerability Scanners, VRM tool).
- Leverage automation services: If security platforms lack API access, use automation services like Zapier or Microsoft Power Automate to push email notifications or event logs into a centralized database (like a Google Sheet or database) that the dashboard tool can read.
- Software recommendations: Purpose-built dashboard applications like Geckoboard or Klipfolio are effective plug-and-play solutions for data visualization.
Step 4: Design for impact and actionability
Good visualization transforms raw data into easily comprehensible stories.
- Layout and hierarchy: Place the most important data (e.g., security risk score, server uptime) in the top-left area of the dashboard, where the eye naturally begins to scan.
- Visualization types:
- Use Line Charts to show performance trends (e.g., MTTR over the last 12 months).
- Use Risk Gauges or Heatmaps to highlight current risk scores against defined thresholds, applying color-coding (e.g., red for a breach of baseline).
- Avoid complex pie charts when displaying many small variables, as they lose functionality and become visually crowded.
- Ensure consistency: To allow for accurate trend analysis, ensure the data is collected in the same way, over the same period, for every reporting cycle.
Practical examples and use cases
The true value of cybersecurity metrics is realized when they drive tangible security improvements and influence business strategy. By focusing on the right KPIs, security teams can effectively justify investments and demonstrate risk reduction.
Here are real-world examples illustrating how categorized metrics lead to actionable results:
Use Case 1: Justifying a budget increase (Strategic focus)
A Chief Information Security Officer (CISO) at a financial firm needed to replace a legacy vulnerability scanner but faced budget scrutiny. Instead of presenting technical details, they used a strategic, cost-related KPI.
- The metric: Return on security investment (ROSI), calculated using quantified risk exposure.
- Actionable insight: The firm used a quantitative risk model to determine that the legacy system left them exposed to an estimated $$$4 million in potential annual losses from unmitigated, known vulnerabilities.
- Result: By demonstrating that the new $$$500,000 scanner would mitigate 90% of that risk (a $$$3.6 million loss avoidance), the CISO presented a clear ROSI of $7.2:1 (($3.6M - $0.5M) / $0.5M). The project was immediately approved, proving the investment's financial viability.
Use Case 2: Improving incident response efficiency (Operational focus)
A large e-commerce company struggled with high dwell time for malware incidents, increasing their potential for data exfiltration.
- The metric: Mean Time to Resolve (MTTR) and Mean Time to Contain (MTTC).
- Actionable insight: The SOC dashboard showed that their median MTTR was 48 hours, significantly higher than the acceptable internal baseline of 24 hours. Analysis revealed the longest step was manual containment (isolating the endpoint).
- Result: The team invested in a Security Orchestration, Automation, and Response (SOAR) platform to automate the isolation process. By automatically isolating an infected machine, they reduced their MTTC by 60% and brought their median MTTR down to 19 minutes—a nearly perfect score for that threat category.
Use Case 3: Enhancing compliance posture (Healthcare industry)
A healthcare provider was preparing for a mandatory audit requiring strict adherence to patch management regulations (e.g., HIPAA and CMMC).
- The metric: Patch Latency (Operational) and Unremediated High-Risk Audit Findings (Compliance).
- Actionable insight: Initial monitoring revealed that critical system patches, especially those from external vendors, often sat unapplied for 30–45 days, creating a large window of opportunity for attackers. The compliance dashboard showed a growing count of open high-risk findings related to this delay.
- Result: The security team implemented a policy mandating critical patch latency to be under 72 hours, as per industry best practice. By prioritizing vulnerability remediation based on severity (CVSS score) and actively tracking compliance, they reduced their average Patch Latency to under a week and achieved a 100% remediation rate for critical audit findings before the audit date.
Frequently asked questions about cybersecurity metrics
What are the most important cybersecurity metrics?
The most important metrics are those that are quantifiable, align with your business goals, and are easy for non-technical stakeholders to understand. They can be grouped into time-based performance and risk exposure:
- Operational & timeliness (The SOC focus):
- Mean time to respond (MTTR): Measures incident response efficiency and recovery speed.
- Mean time to contain (MTTC): Measures how quickly an incident is isolated to prevent further spread.
- Patch latency: The speed at which security teams apply critical vendor patches.
- Risk & Strategic (The Board Focus):
- Quantified risk exposure: Translates technical risk into a clear financial estimate of potential loss.
- Average vendor security rating: Provides an objective, real-time assessment of third-party risk.
- Phishing click-through rate: Quantifies the human risk factor, which is a major attack vector.
How do I present cybersecurity metrics to the board?
Board members primarily focus on information that impacts revenue, brand reputation, and financial stability. To present effectively:
- Focus on business impact, not volume: Boards generally do not want raw technical data like the number of firewall blocks or detailed phishing rates. Focus instead on what had a business impact.
- Use financial and peer benchmarking: Report on easily digestible KPIs like Quantified Risk Exposure and Company vs. Peer Performance to provide context and financial translation of risk.
- Address key board questions: Be prepared to answer questions about the likelihood of a significant breach, expected recovery time from a major incident, and steps taken to mitigate third-party risks.
- Lead with an executive summary: Start the dashboard or report with a concise paragraph that summarizes the security posture and sets the overall narrative.
Can I automate cybersecurity metric tracking?
Yes, automating metric tracking is essential for achieving the accuracy and speed needed for modern security reporting.
- SOAR/SIEM tools: Security Orchestration, Automation, and Response (SOAR) and Security Information and Event Management (SIEM) platforms automatically log timestamps for key events, allowing for accurate, automated calculation of time-based metrics like MTTR and MTTD.
- Data consolidation: Automation services (e.g., Zapier) can be used to extract data from various security platforms and push it to a central database or dashboard tool, consolidating multiple data sources into a single view.
- Continuous reporting: Automation ensures consistency by collecting data the same way over similar time periods, which is vital for effective trending and analysis.
Conclusion and next steps
Cybersecurity metrics and KPIs are the foundation of a proactive, defensible security program. By transitioning from purely technical metrics (raw counts) to strategic KPIs (rates, averages, and financial estimates), organizations can achieve unparalleled visibility and communicate the value of security to the entire business.
The value of choosing the right metrics
Choosing the right metrics is critical because they:
- Inform strategic decisions: They align security operations with the C-suite’s financial and risk appetite, allowing leaders to invest strategically rather than reactively.
- Drive operational efficiency: Time-based metrics (MTTD, MTTR, MTTC) reveal operational bottlenecks and justify automation, resulting in a more efficient and faster-responding SOC team.
- Ensure compliance: Compliance KPIs provide concrete evidence of adherence to regulatory standards (NIST, GDPR), transforming GRC from a periodic headache into a continuous, measurable activity.
Your next steps to a metrics-driven program
To build a more strategic and defensible security program, start here:
- Categorize your existing data: Take your current raw security metrics and map them to the four categories: Operational, Strategic, Compliance, and VRM.
- Select your foundational KPIs: From each category, choose one Key Performance Indicator (KPI) or Key Risk Indicator (KRI) that directly relates to a current organizational priority (e.g., choose Patch Latency if vulnerability management is a focus, or Average Vendor Security Rating if third-party risk is a concern).
- Build your dashboard: Consolidate these chosen KPIs into a simple, dedicated dashboard using visualization tools, focusing on clear trends and actionability for your primary audience.
- Prioritize financial reporting: Work with risk management teams to translate key risks into Quantified Risk Exposure figures to establish a powerful, business-centric reporting narrative for the board.
While there's no single standard for selecting the right Vendor Risk Management KPIs and KRIs, your choice should align with your specific industry, security needs, regulatory requirements (like NIST, GDPR, or HIPAA), and your overall appetite for risk. Remember that all chosen metrics must be clear to non-technical stakeholders—a good rule is to pick new metrics or improve your explanation if they aren't immediately understandable, often by using benchmarks and industry comparisons.
Finally, when presenting to executives, focus primarily on the financial impact of your efforts, demonstrating how cybersecurity is actively saving the organization money, ideally supported by a cybersecurity executive report.