On April 4, 2025, The Australian Financial Review reported on a set of credential abuse attacks targeting multiple Australian superannuation funds. These attacks were not breaches of the infrastructure of those companies, but compromises of individual customer accounts via stolen credentials. How were those customer credentials stolen? The UpGuard Research team compared the number of affected accounts to the number of customer identities in infostealer logs over the past year and found evidence that this common method of credential compromise may have contributed to the account breaches. Furthermore, it suggests that effective monitoring of dark web data can help prevent such attacks from succeeding in the future.

A Complete Guide to Data Breaches
Download this eBook to learn how to avoid a costly data breach with a comprehensive prevention strategy.
A Coordinated Attack on Superannuation Funds
As reported by the AFR, “major industry funds Australian Retirement Trust, AustralianSuper, REST and Hostplus were all breached. Insignia, the owner of the 180-year-old MLC brand and the largest retail superannuation fund, also suffered a cyberattack.”
Not all companies have been affected equally. Thus far only AustralianSuper has confirmed customers losing money–around $100,000. The other funds have reported attackers targeting customer accounts but no losses. As we will see, AustralianSuper is also the company with the greatest exposure of customer passwords via infostealers.
In addition to disclosing whether customers lost any money, several funds also shared the number of customer accounts impacted in the attacks. The AFR reported 600 AustralianSuper accounts breached, 100 Insignia accounts, and up to 8000 REST accounts. Knowing the approximate number of accounts affected for each super allows us to compare that number to the number of customer passwords stolen by infostealer malware to determine whether that is a plausible vector in this attack.
The Growing Threat of Infostealer Malware
UpGuard monitors the dark web for credentials captured in infostealer (or just “stealer”) logs. The entries in infostealer logs include the user’s email or username, password, and the web address for the login page. Monitoring infostealer data can thus tell a company when its employees or customers have had their passwords compromised. Passwords and other credentials collected by infostealers have been the cause of many recent high profile breaches, including those of AT&T, Ticketmaster, and Santander.
The number of accounts breached in the coordinated attack on these Australian superannuation funds is strikingly similar to the number of users for each service in stealer logs over the last year.

A Complete Guide to Data Breaches
Download this eBook to learn how to avoid a costly data breach with a comprehensive prevention strategy.
Comparing Affected Accounts to Compromised Users
To start, we queried stealer logs including the login domains for each of the affected super. Insignia is here represented by their superannuation brand mlc.com.au. The member login for REST is on the domain aas.com.au.
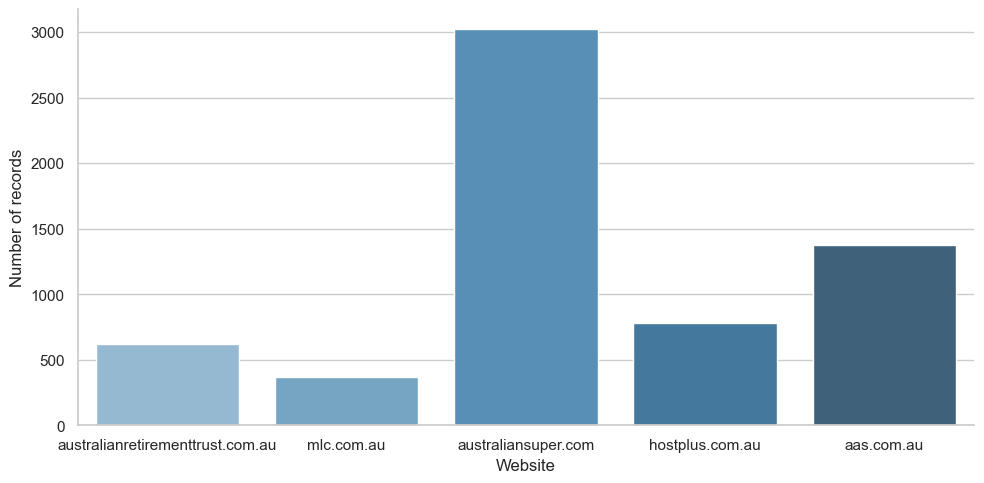
The raw number of stealer logs mentioning each domain is around 300-3000 records for each company. While each of the records in UpGuard’s dark web database is unique, some are partial records that might include an identifier like device id but not the user’s email address. Records that are logically unique might also functionally overlap, like if the same user was compromised on multiple devices, or if a user's email address was included in one record and then later exposed again with the same email address and more information about them. To get a clearer picture of how many customers were actually exposed for each super fund, we narrowed the data down to records with a unique email address or a unique username.

AustralianSuper had a reported 600 customers affected in the attack; over the last year, they had about 1000 customer credentials exposed via stealer logs. Insignia (MLC) reported 100 customers affected with about 150 customer credentials exposed. Those two sets of numbers are proportionally very similar, and when we factor in the assumption that some of those credentials would have been changed in the last year, the absolute numbers are quite close as well. Based on the data from these incidents, the number of customers in infostealer records is a useful predictor of number of customer accounts impacted in an attack.
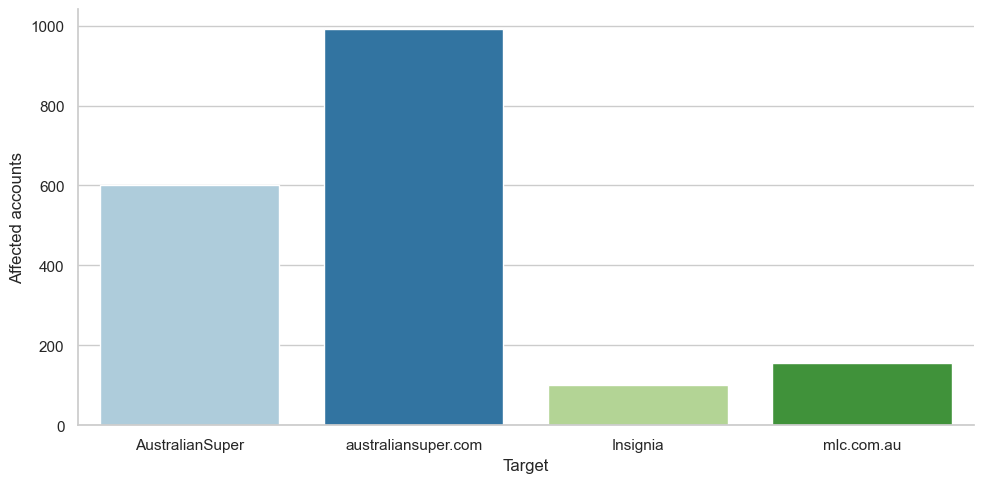
The number of accounts reported by REST (aas.com.au), on the other hand, is much higher than the number of customer passwords in stealer logs and about ten times the number of accounts affected at AustralianSuper. REST reported 8000 accounts affected; we see closer to 700 customer passwords in the stealer logs. This discrepancy may indicate that those accounts were being targeted with more brute force attacks like password spraying, or that the other superannuation funds who reported much lower numbers were effectively able to filter out those attacks and did not count them in the number of customers impacted.
What Companies Can Do
Without knowing the identities of the people affected, there is no way to confirm whether the credentials in these stealer logs correspond to the individuals affected. However, when we see two companies where the number of affected accounts is so close to the number of identities exposed, it’s clear why monitoring for infostealer exposure has become a must-have capability for threat intelligence teams. Customer credentials are being traded for hundreds of customers of these superannuation funds every year. Companies can monitor for those exposures and reduce the likelihood of impact to their customers.
Additionally, multi-factor authentication is a vital defense against account compromise. There are no silver bullets, but MFA introduces a significant barrier to abusing credentials. MFA should be a requirement for any application with access to anything of value, whether that be sensitive personal information, corporate secrets, or bank funds. These attacks should serve to illustrate why both multifactor authentication and robust threat monitoring are worthwhile practices to maintain customer trust.




